Nevis Mobile Authentication
Nevis Mobile Authentication builds up on top of the FIDO UAF 1.1 protocol and supports the registration, authentication, transaction confirmation and deregistration operations of FIDO UAF 1.1. It enables secure and convenient authentication for relying applications by letting users verify their identity via their mobile device. This is achieved by integrating the relying web applications with the Nevis Security Suite and implementing Nevis Mobile Authentication client-capabilities in a mobile application.
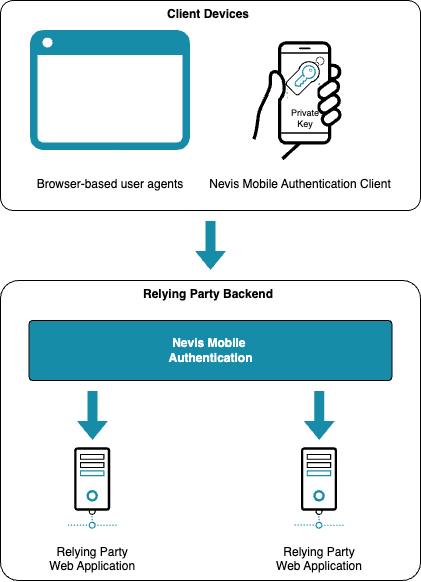
The Nevis Mobile Authentication server-side is based on Nevis components including nevisIDM as the Identity Management System. This ensures end-to-end compatibility and decreases integration efforts with third-party components. For more details on the server-side architecture, see the High-Level Architecture.
Mobile Authentication Devices
Nevis Mobile Authentication focuses on mobile devices with FIDO Client capabilities and FIDO Authenticators. To connect the FIDO Clients and the FIDO Authenticators with the server-side of Nevis Mobile Authentication, a small communication layer must be implemented in the Relying Party client application. This abstraction layer is referred to as Nevis Mobile Authentication client. The Nevis Mobile Authentication client is responsible to communicate FIDO UAF protocol messages received by the mobile application to the FIDO Client and from the FIDO Client to the Relying Party.
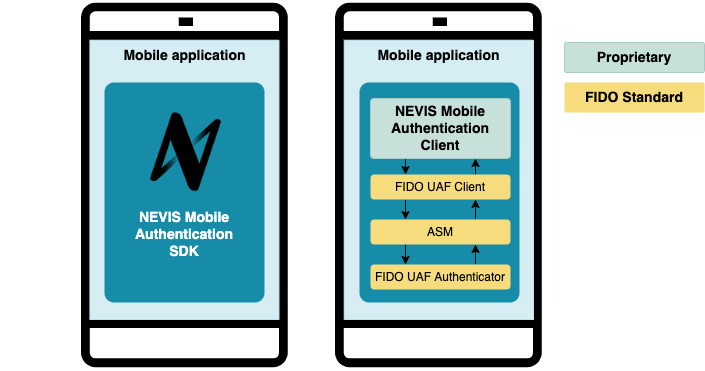
To allow quick and easy development of mobile applications with support of Nevis Mobile Authentication, Nevis Mobile Authentication Client SDKs for Android, iOS, Flutter and React Native are available.
Nevis Mobile Authentication anticipates two integration scenarios for the Nevis Mobile Authentication client on the mobile device:
- A Nevis Mobile Authentication client built into a mobile Business Application which requires authentication (built-in).
- A Nevis Mobile Authentication client built into a dedicated native mobile application solely built to implement authentication, transaction confirmation, registration and deregistration scenarios (Access App).
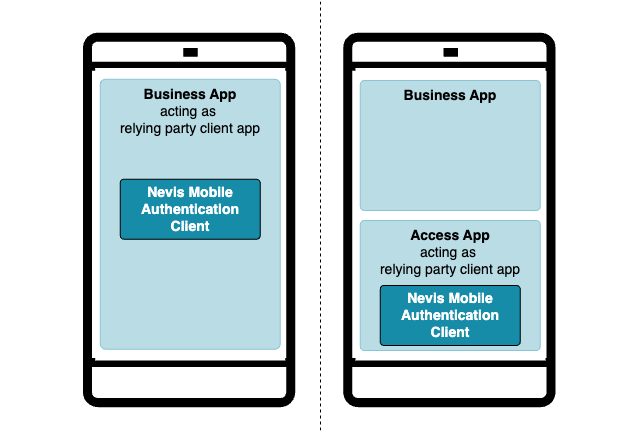
If Nevis Mobile Authentication client capabilities are built into a business application, FIDO protocol messages between the server-side and the client-side may be directly transferred through established communication channels. If Nevis Mobile Authentication Client capabilities are built into a separate dedicated application for authentication,an out-of-band channel must be used to establish a new communication channel between the server-side and the mobile application.
Based on the client-side integration type, Nevis Mobile Authentication thus supports two authentication concepts.