Reference Deployment
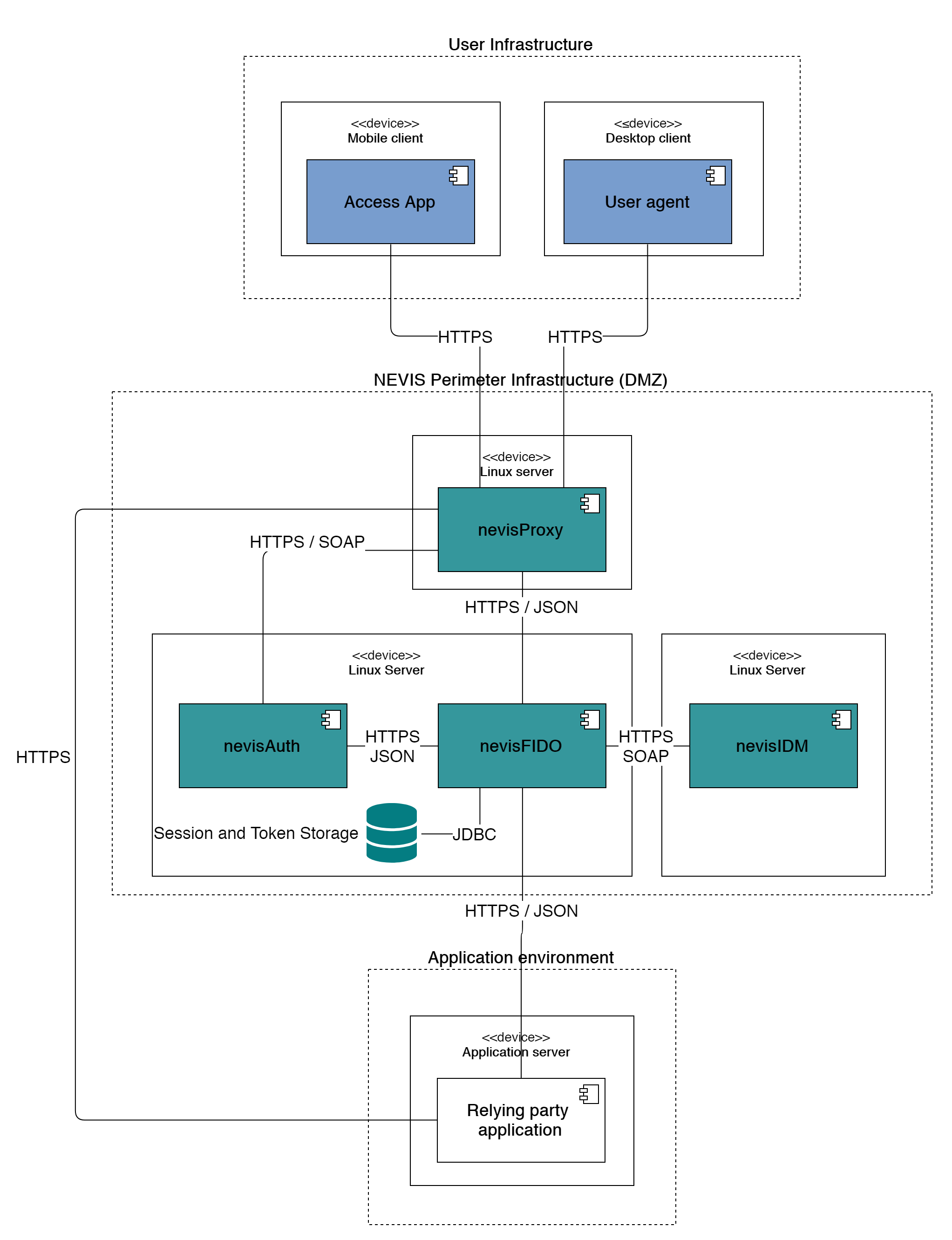
Minimal Recommended Physical Deployment Infrastructure
The figure shows a typical, minimal deployment of the Nevis Mobile Authentication solution. The perimeter infrastructure consists of a Linux Server environment running nevisProxyto protect access to the internal application environment. This in term is split into two servers, one running the relying party application, the other one running the authentication environment consisting of nevisAuth and nevisFIDO and the identity management environment, consisting of nevisIDM.
Note that this solution outline does not provide load balancing capabilities.
Scaling
Performance related scaling of the infrastructure can be achieved by vertical or horizontal scaling. Vertical scaling refers to increasing the hardware resources of the involved components (CPU, RAM). For more information regarding hardware and software requirements, see the System Requirements chapter.
Horizontal Scaling
Horizontal scaling can be achieved by using a shared, database backed session and token storage.
Multiple scaling setups are possible, the following figure outlines the two most likely ones:
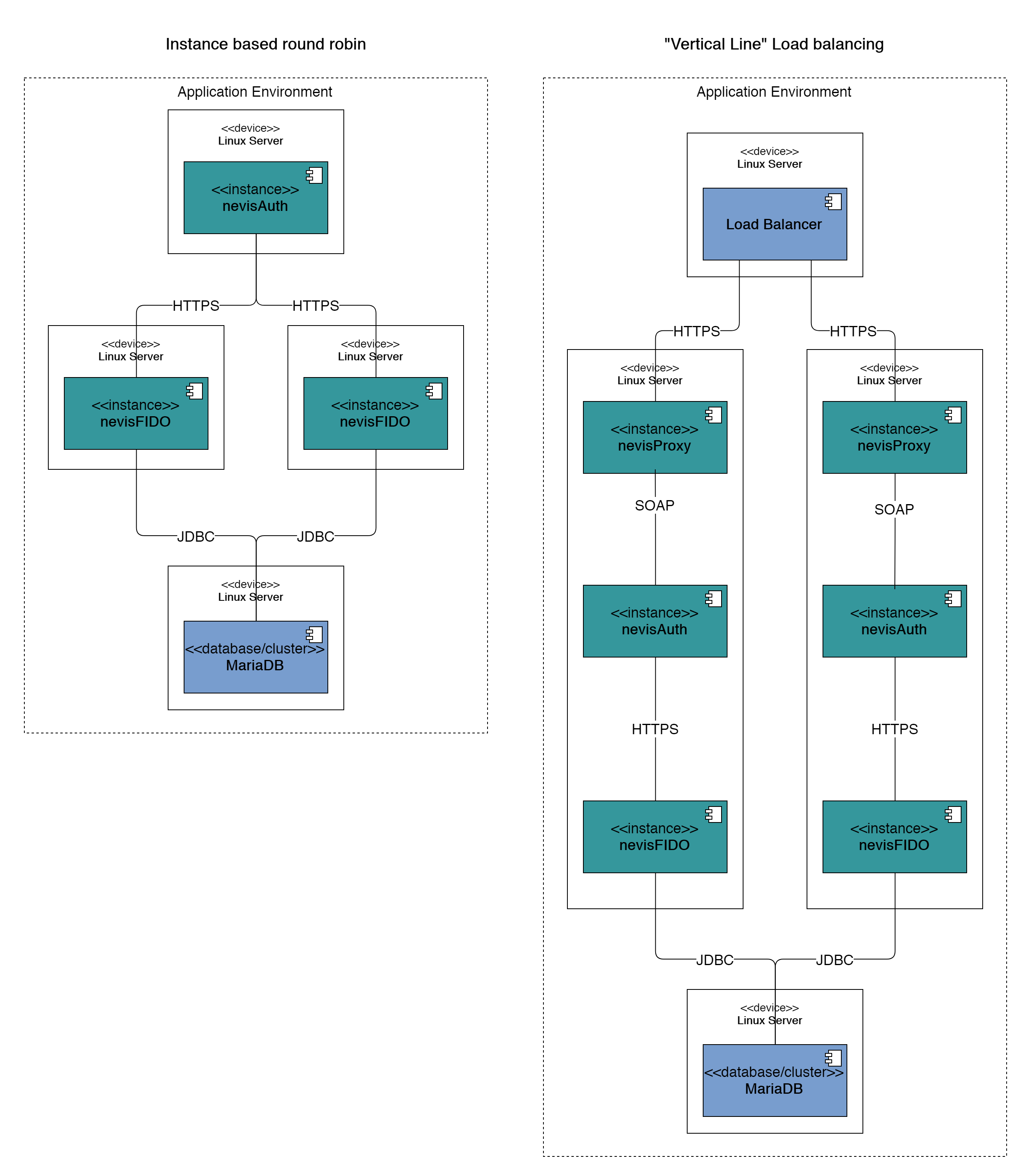
- In the instance based round robin approach, one nevisAuth instance is configured to connect to two nevisFIDO instances using round robin.
- In the "vertical line" load balancingapproach, a dedicated load balancer is used to balance the incoming requests between two (or more) complete Nevis authentication suite setups. In this example, the load balancer is placed in front of nevisProxy,however it can potentially be placed at different levels as well.