Concept Description and Technical Architecture
The nevisAppliance is the recommended Linux platform for Nevis software. The nevisAppliance provides an opinionated and fixed set of pre-installed packages and configuration, it is not meant as general purpose Linux.
It uses the CentOS/64bit operating system configured for optimal performance, and features adequate security settings to be used within DMZ and secure network zones.
The nevisAppliance can be used in two different configurations. When used as a hardware appliance, the software is directly installed on the server's disk. As a software appliance, it is delivered as a CDROM (ISO) image which has to be installed in a virtual server (VMware ESX).
File system
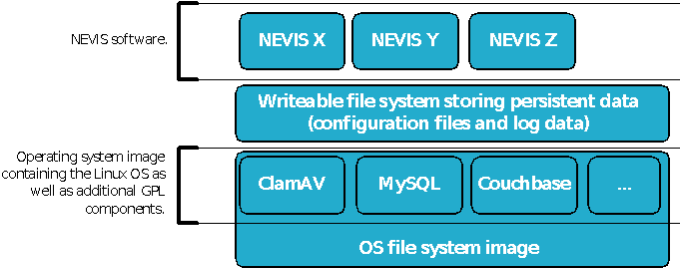
The nevisAppliance uses an overlay file system which consists of multiple layers.
The lowest level contains the operating system (OS). It is a single squashfs image file mounted to the "/" mount point. This image contains all operating system files (/bin, /usr, …) as well as third party software components, such as the MySQL database or the ClamAV virus scanning engine. The scope of available software within this layer depends on the image type you have chosen, see the chapter "Image types". This layer is going to be replaced whenever you install a new
neviscd2_<version>os<type>.imgfile.The operating system image is transparently overlaid by a writable file system storing all persistent data, such as all your configuration and log files. Every file, symbolic link and empty directory not listed within the
/etc/rwdisk.conffile is going to be deleted when rebooting the server. Thus, do not install any additional software packages (rpm), or they will get lost once you reboot the server.The third layer includes the Nevis products and component images. Each Nevis product or component is packed into a single read-only file system and all those image files are mounted to the
/opt/nevis*directories. This layer is updated by installing a newneviscd2_<cluster version>nevis<type>.imgfile.
Reference architecture
A nevisAppliance is able to host different Nevis software. You choose which product or component to use by creating an instance of the required product or component.
Figure below Sample network diagram shows two appliances. One is located within the DMZ hosting nevisProxy instances, while the second one is located within the secure server network called "Application Zone" hosting a nevisAuth instance.
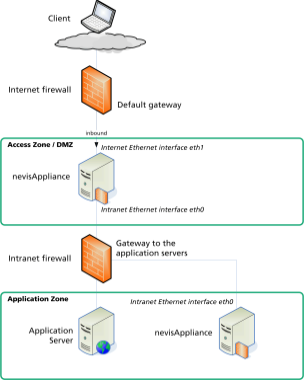
The nevisAppliance within the DMZ uses two Ethernet interfaces:
The intranet Ethernet interface (eth0) is connected to the internal firewall. It is used for the communication from the nevisAppliance to the application servers as well as for the administrative network traffic from the management server to the nevisAppliance. You can add routes to the intranet servers using the nevis-appliance command (see the chapter "Server configuration").
The internet Ethernet interface (eth1) is connected to the external firewall. It is used for connections from clients using the web applications to the nevisAppliance. The default route is normally configured using the router attached to this interface.
The nevisAppliance within the "Application Zone" uses one Ethernet interface:
- The internal Ethernet interface is used for application and administrative network traffic.
Communication ports
Figure below Default ports shows the default ports Nevis product or components commonly use for communicating with each other.
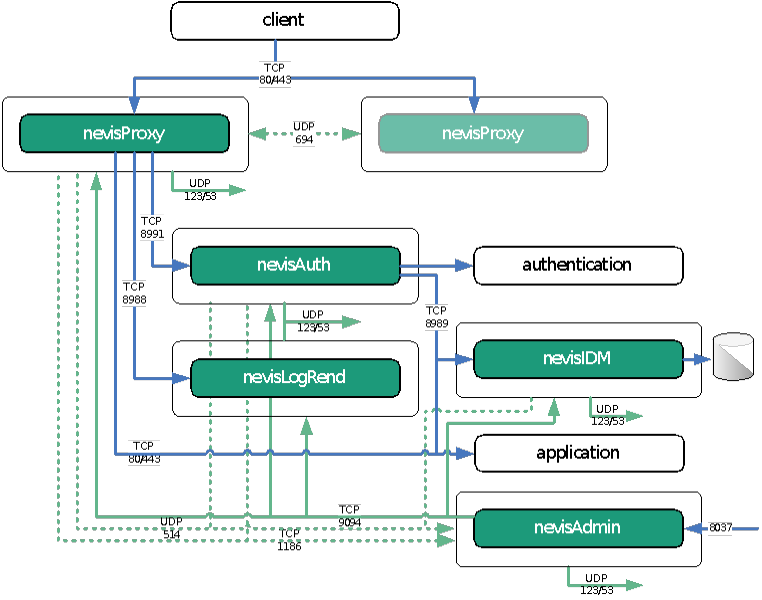
| Port | Protocol | Usage |
|---|---|---|
| TCP 80/443 | HTTP and HTTPS | The standard ports for HTTP(S) traffic. |
| TCP 8991 | SOAP over HTTPS | The communication between nevisProxy and nevisAuth. |
| TCP 8988 | HTTP | The communication between nevisProxy and nevisLogRend (usually, nevisLogRend is located on the same server as nevisProxy and is listening on the local loopback interface (localhost)). |
| TCP 8989 | SOAP over HTTPS | The communication between nevisAuth and nevisIDM. Can also be used to access the web front end of nevisIDM via nevisProxy. |
| UDP 694 | Failover heartbeat | Heartbeat messages exchanged between the nevisAgent instances. |
| TCP 9094 | HTTPS | Communication between nevisAdmin and nevisAgent (to every host). |
| UDP 123UDP 53 | NTP and DNS | NTP and DNS packages are sent to the central NTP and DNS servers. |
| UDP 514TCP 10514 | Syslog over UDP or TLS | Every server may forward log messages to the nevisAdmin server. |
| TCP 1186 | MySQL Cluster | The NDB nodes on nevisProxy and/or nevisAuth need to connect to the server hosting the management node. |
| TCP 22 | SSH | You may want to enable SSH access from the intranet or dedicated administration workstations to any server hosting Nevis products or components. |
| TCP 8037 | HTTPS | Web access to nevisAdmin (by the administrator). |