Distributing the token signer public key
The signer's certificate has to be accessed by clients that use, and therefore need to verify, the security token. This public key is not security-sensitive data. However, the installation itself is an authorization step, because the client is enabled to validate and except the security token.
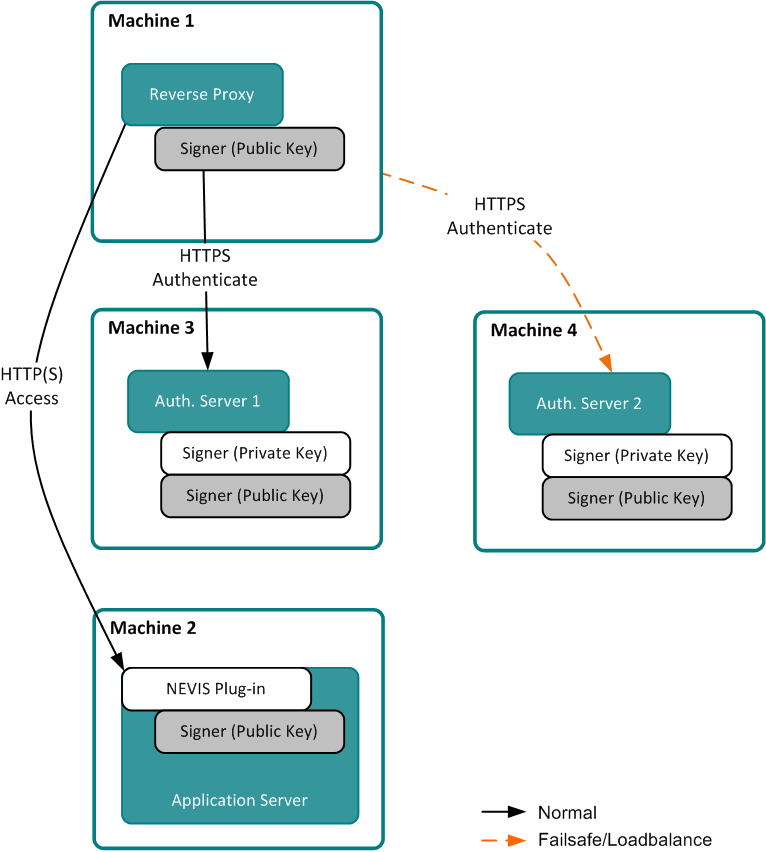
The following figure shows a symbolic setup of the key distribution for one reverse proxy (Machine 1), using a nevisAuth installation in failsafe/loadbalancing mode (Machine 3 and Machine 4), and a content provider (Machine 2):
How to export the nevisAuth signer key depends on how the signer certificate was created and installed "):
- By using built-in simple soft certificate management. In this case, run the following command:
# nevisauth signer export
- By using nevisKeybox. In this case, the files are readable without a special export command. Locate the required files by running:
# neviskeybox list
Because key handling is usually considered to be tricky, refer to the nevisKeybox reference guide for further information and assistance.
For further information on how to configure the nevisAuth signer's public key for token verification, refer to the nevisProxy reference guide, the chapter on Configuring User Authentication.