Integration without nevisProxy
To access nevisMeta via REST API without using nevisProxy, the user must use one- or two-way TLS to identify themselves, with a X509 certificate that includes the role attribute.
How does it work
nevisMeta checks the role attribute in the X509 certificate to define the next action regarding the user:
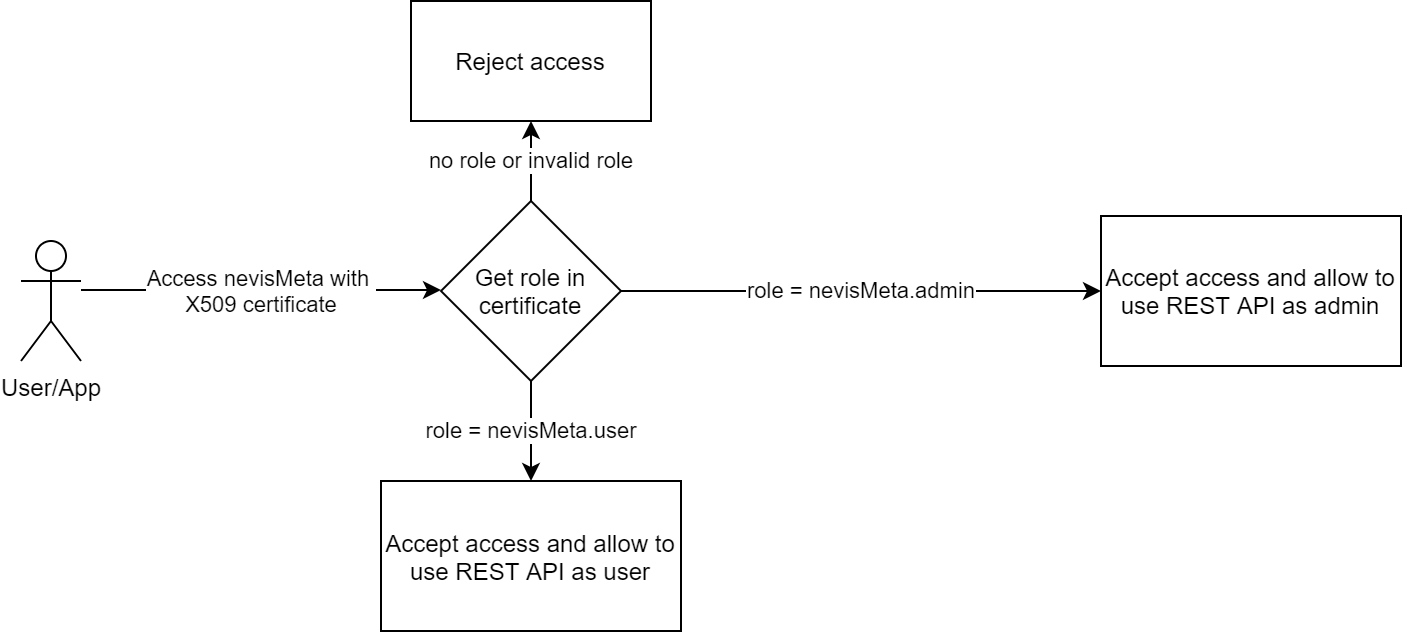
How to enable two-way TLS
By default, nevisMeta requires one-way TLS to connect. You can enable two-way TLS by updating the property server.tls.require-client-auth=true in the configuration file nevismeta.properties.
How to create a certificate with the role attribute
Via nevisKeybox
- Create a root CA if it does not exist yet:
neviskeybox cacreate -ca nevismeta -subject 'cn=nevisCA, o=Nevis Security AG, c=ch' -batch
- Create a certificate request:
neviskeybox certreq -slot nevismeta -label admin -subject 'cn=nevis.net, role=nevisMeta.admin, o=Nevis, c=ch' -subjectAltName 'DNS:nevis.net' -batch
- Edit the file openssl.conf to allow adding a role to the X509 certificate:
/var/opt/neviskeybox/default/nevismeta/openssl.conf
[ policy_anything ]
role = optional
....
[ req_distinguished_name ]
role = 'role'
- Sign the certificate request with the existing CA:
neviskeybox sign -ca nevismeta -out /tmp/nevismeta_admin_new_cert.pem -file /var/opt/neviskeybox/default/nevismeta/admin_request.pem -batch
- Import the certificate into the keybox:
neviskeybox import -file /tmp/nevismeta_admin_new_cert.pem -batch
- Verify the certificate:
# openssl x509 -noout -text -in /var/opt/neviskeybox/default/nevismeta/admin_keystore.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 0 (0x0)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = ch, O = Nevis Security AG, CN = nevis.net
Validity
Not Before: Mar 26 14:39:54 2021 GMT
Not After : Mar 24 14:39:54 2031 GMT
Subject: C = ch, O = Nevis Security AG, CN = nevis.net, role = nevisMeta.admin
...
Via openssl
Add the openssl.conf file:
openssl.conf
# Nevis key box openssl config
RANDFILE = ./.rand # private random number file
[ ca ]
default_ca = CA_default # The default ca section
[ CA_default ]
dir = ./ # Where everything is kept
certs = $dir # Where the issued certs are kept
crl_dir = $dir # Where the issued crl are kept
database = $dir/index.txt # database index file.
new_certs_dir = $dir # default place for new certs.
certificate = $dir/ca_cert.pem # The CA certificate
serial = $dir/serial # The current serial number
crl = $dir/crl.pem # The current CRL
private_key = $dir/ca_key.pem # The private key
x509_extensions = node_cert # The extentions to add to the cert
name_opt = ca_default # Subject Name options
cert_opt = ca_default # Certificate field options
default_days = 3650 # how long to certify for (signed cert validity)
default_crl_days = 30 # how long before next CRL
default_md = sha256 # which md to use.
preserve = no # keep passed DN ordering
unique_subject = no # openssl 0.9.8 feature for cert rollover
policy = policy_anything
email_in_dn = yes
copy_extensions = copy
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
uid = optional
role = optional
[ v3_ca ]
basicConstraints = CA:true
subjectKeyIdentifier =hash
authorityKeyIdentifier =keyid,issuer:always
[ user_cert ]
basicConstraints =CA:FALSE
nsComment = "Nevis Generated Certificate using OpenSSL"
keyUsage = digitalSignature, dataEncipherment, keyAgreement, nonRepudiation, keyEncipherment
extendedKeyUsage = clientAuth, emailProtection
# PKIX recommendations harmless if included in all certificates.
subjectKeyIdentifier =hash
authorityKeyIdentifier =keyid,issuer:always
# keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment, keyAgreement
# extendedKeyUsage = codeSigning, serverAuth, clientAuth
# emailProtection, timeStamping, OCSPSigning
# ipsecEndSystem, ipsecTunnel, ipsecUser
#nsCertType = server, client, email, objsign
[ node_cert ]
basicConstraints =CA:FALSE
nsComment = "Nevis Generated Certificate using OpenSSL"
keyUsage = keyEncipherment, keyAgreement, digitalSignature
extendedKeyUsage = serverAuth, clientAuth
subjectKeyIdentifier =hash
authorityKeyIdentifier =keyid,issuer:always
nsCertType = server, client
[ enc_cert ]
basicConstraints =CA:FALSE
nsComment = "Nevis Generated Certificate using OpenSSL"
basicConstraints =CA:FALSE
keyUsage = dataEncipherment
subjectKeyIdentifier =hash
authorityKeyIdentifier =keyid,issuer:always
[ sign_cert ]
basicConstraints =CA:FALSE
nsComment = "Nevis Generated Certificate using OpenSSL"
keyUsage = digitalSignature
subjectKeyIdentifier =hash
[ req_v3_ca ]
basicConstraints = CA:true
#leave this empty -> see v3_ca profile
[ req_user_cert ]
basicConstraints =CA:FALSE
keyUsage = digitalSignature, dataEncipherment, keyAgreement, nonRepudiation, keyEncipherment
extendedKeyUsage = clientAuth, emailProtection
[ req_node_cert ]
basicConstraints =CA:FALSE
keyUsage = keyEncipherment, keyAgreement, digitalSignature
extendedKeyUsage = serverAuth, clientAuth
[ req_enc_cert ]
basicConstraints =CA:FALSE
keyUsage = dataEncipherment
[ req_sign_cert ]
basicConstraints =CA:FALSE
keyUsage = digitalSignature
# required for Solaris openssl
[ req ]
default_md = sha256
distinguished_name = req_distinguished_name
x509_extensions = v3_ca
req_extensions = req_v3_ca
string_mask = default
# nice to have for adhoc CA
[ req_distinguished_name ]
countryName = 'Country Name (2 letter code) '
countryName_default = ch
countryName_min = 0
countryName_max = 2
stateOrProvinceName = 'State or Province Name (full name) '
stateOrProvinceName_default =
localityName = 'Locality Name (eg, city) '
localityName_default =
0.organizationName = 'Organization Name (eg, company) '
0.organizationName_default = Nevis Security AG
0.organizationalUnitName = '1st Organizational Unit Name (eg, section) '
0.organizationalUnitName_default =
1.organizationalUnitName = '2nd Organizational Unit Name (eg, area) '
1.organizationalUnitName_default =
commonName = 'Common Name (eg, YOUR name) '
commonName_max = 64
commonName_default = Nevis Keybox CA: nevis.net (nevis.net)
emailAddress = 'Email Address '
emailAddress_default =
emailAddress_max = 64
role = 'role'
- Create a root CA if it does not exist yet:
openssl req -config ./openssl.cnf -new -x509 -keyout ./ca_key.pem -out ./ca_cert.pem
- Create a certificate request:
openssl req -new -config openssl.cnf -key ca_key.pem -out req_admin.pem
- Sign the certificate request with the existing CA:
openssl ca -config openssl.cnf -extensions v3_ca -policy policy_anything -out admin_cert.pem -infiles req_admin.pem
- Verify the certificate:
# openssl x509 -noout -text -in admin_cert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 0 (0x0)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = ch, O = Nevis Security AG, CN = nevis.net
Validity
Not Before: Mar 26 14:39:54 2021 GMT
Not After : Mar 24 14:39:54 2031 GMT
Subject: C = ch, O = Nevis Security AG, CN = nevis.net, role = nevisMeta.admin
...