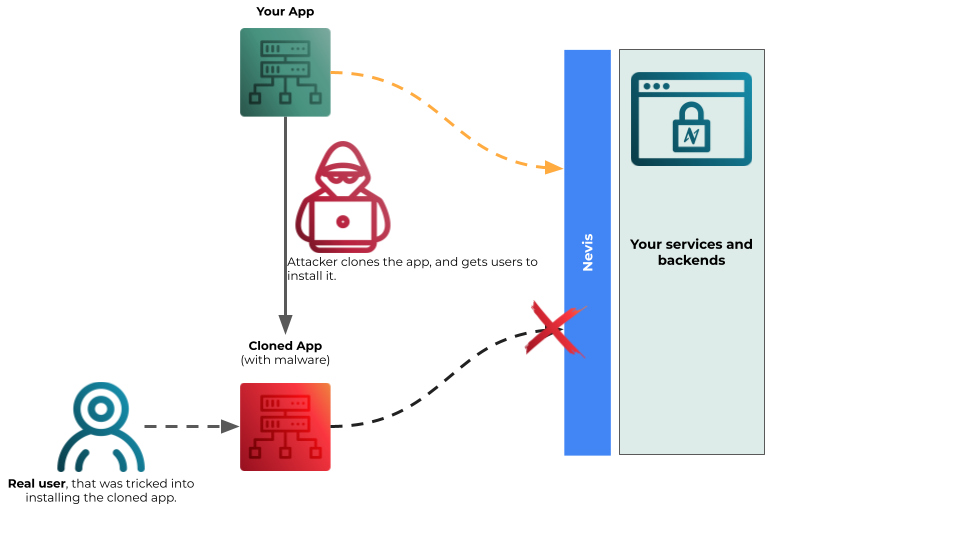
Application Attestation
The nevisFIDO component allows to verify the client performing a FIDO UAF registration, authentication or transaction confirmation is a known application, also known as "app attestation". This ensures that only trusted applications can register and authenticate using FIDO UAF.
In Android, the nevisFIDO component uses the Google Play Integrity API to validate the Application integrity. In iOS, nevisFIDO uses the Apple DeviceCheck services.
Protections offered by app attestation
Prevents app-based fraud / fake apps
By verifying an app's authenticity, attestation helps to prevent fake or repackaged versions of an app designed to steal user data, credentials, or financial information.
Safeguards content
For apps that offer paid content or subscriptions, attestation prevents unauthorized access by ensuring that only legitimate, unmodified versions of the app can request access to these resources.
Requirements
The Application Attestation only works with mobile applications using the Nevis Mobile Authentication SDK 4.x or later and nevisFIDO 8.2505.x RR or later. The requirements for each platform are mentioned below.
The (iOS) app attestation feature is currently not supported when using nevisIDM with OracleDB database. Nevis intends to introduce support for OracleDB with the May 2026 release.
Android
- The mobile app must be published to the Google Play Store.
- A Google Cloud Account with the Google Integrity API enabled is required. The account information must be provided in the nevisFIDO configuration.
- nevisFIDO must have access to the Google Cloud Play Integrity APIs. That is, nevisFIDO must be able to do HTTP requests against the URL
https://playintegrity.googleapis.com. - The Google Cloud Project Number (not the project ID) must be provided to the Nevis Mobile SDK Configuration.
iOS
- The mobile app must be published to the Apple App Store.
- The iOS Team Identifier and the iOS DeviceCheck Key must be configured in the nevisFIDO configuration.
- nevisFIDO must have access to the Apple servers to perform the App integrity check:
- For applications deployed in production environments, nevisFIDO must have access to
https://data.appattest.apple.com/v1/attestationData. - For applications deployed in development environments, nevisFIDO must have access to
https://data-development.appattest.apple.com/v1/attestationData.
- For applications deployed in production environments, nevisFIDO must have access to
Facet ID
In addition to validating that the application is published in the Google Play Store and in the Apple App Store, nevisFIDO will also check that the application is listed in the trusted facets.
This implies that the bundle of the iOS applications must be listed in the facets configuration, and that in the case of Android, the APK key hash of the trusted applications must be included in the facets list. Example:
fido-uaf:
facets:
- "android:apk-key-hash:<hash-of-apk-signing-cert>"
- "ios:bundle-id:<ios-bundle-id-of-app>"
This also implies that you cannot use wildcard facet IDs (which are intended for development purposes) with Application Attestation.
See the nevisFIDO Facets Service and the Nevis Mobile SDK Facet ID chapters for details regarding the facets in both nevisFIDO and in the mobile client.
The nevisFIDO policy (see below) allows to restrict the trusted applications even further when requiring Application Attestation. If this feature is used, only applications included in this additional list and in the facets will be accepted.
Enabling application attestation for FIDO UAF registration and authentication
Visit the nevisFIDO application attestation installation guide for the component configuration instructions.
Whether Application Attestation is required for a given operation and authenticator is specified using the FIDO UAF Policy. This provides you with the flexibility to require Application Attestation for some operations and not for others.
The Application Attestation validation implies that nevisFIDO contacts Google and Apple Servers, this can impact the time required to process the operations. This performance and resource usage impact should be considered when using application attestation. To reduce the impact, you can define a policy for registration that requires application attestation and one for authentication and transaction confirmation that does not. If application attestation is used for FIDO UAF credential registration, you have the guarantee that those credentials have been created and stored in a trusted application. Moreover, since the FIDO UAF credentials are stored by the mobile client in a secure environment, only that application will be able to authenticate with those credentials.
The policy configuration examples show you how to configure the Application attestation in the FIDO UAF policy.
Comparison with FIDO UAF Full Basic Attestation
For Android, nevisFIDO supports FIDO UAF Full Basic Attestation. Full basic attestation and application attestation serve a similar purpose: server-side validation of specific client properties, however they differ in terms of what they verify:
Application Attestation
- Verifies that the client is an application published in Google Play.
- Can verify that the application package is one of those listed in the policy.
- Verifies that the application is signed with the developer certificate.
Android FIDO UAF Full Basic Attestation
- Verifies that the FIDO UAF keys are stored in a Google certified chipset.
- Verifies that the chipset has not been compromised.
- Verifies that the application has been signed with the developer certificate.