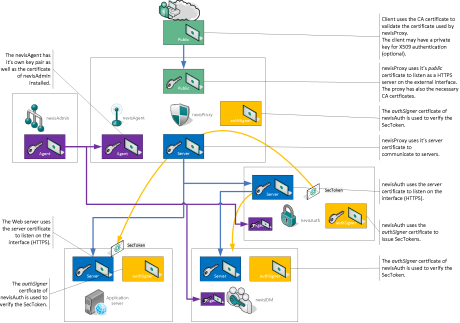
Key management
We identify the following key material:
- Server: Typically, each server has its own private key and certificate. This key material is used to establish secure connections to other components, e.g., when a nevisProxy connects to a nevisAuth instance or when nevisAuth connects to an LDAPS server (see the chapter Key material per server about how to manage this key material with nevisAdmin).
- Public: nevisProxy requires public key material to allow clients (browser) to establish secure SSL connections (see the chapter nevisProxy key material about how to manage this key material with nevisAdmin).
- authSigner: The authSigner keys are used within an SSO realm. Every nevisAuth instance involved in a realm should use the same private key and certificate to issue user authentication tokens, such as the Nevis SecToken, or SAML assertions. nevisProxy uses this key material to verify the SecToken (see the chapter Key material per realm about how to manage this key material with nevisAdmin).
- nevisAgent: Every nevisAgent requires a valid certificate to allow nevisAdmin to communicate with the nevisAgent, see the chapter nevisAgent software installation.
Key material is either managed for each server and Nevis component individually by using the server's nevisKeybox instance at the command line interface, or by using the web front-end of nevisAdmin.
Key material is referred by slot and label names and the keys and certificates are stored in keystores (private key and certificate) and truststores (certificates only, e.g., CA root and CA intermediate certificates).