Security
The following actors are important from a security point of view:
- The user accessing the administration web application, nevisDetect Web App. The nevisDetect Web App is an Angular 2 based Single Page Application (SPA) running in the browser of the user.
- The components of nevisDetect accessing others components.
In most environments a set of (security) roles are assigned to an identity (an identity can be e.g., a user). To be able to integrate your enterprise environment seamlessly into nevisDetect, nevisDetect maps the security roles onto permissions, as you can see in the figure Role-permission-mapping below:
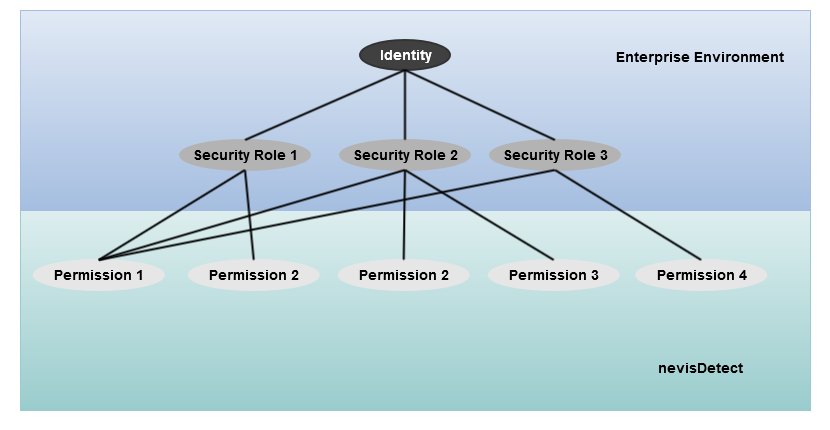
From now on, we call this mapping within nevisDetect role-permission-mapping. nevisDetect ships with a default role-permission-mapping. Use this default mapping as a starting point for your custom mapping configuration.
The default mapping is based on the assumption that for every persona a separate security role exists. Additionally, there are security roles representing the different components of nevisDetect, see the table Personas and security roles below for an overview of all available personas and security roles. This allows an uniform treatment of all actors (users and components) from a security point of view.
| Persona/component | Security role |
|---|---|
| Support desk user (Persona) | DETECT_HELPDESK |
| Security expert | DETECT_SECURITY_OFFICER |
| Operator | DETECT_OPERATOR |
| Forensic expert | DETECT_FORENSIC_EXPERT |
| nevisDetect Core | DETECT_CORE |
| nevisDetect Feature Correlator | DETECT_FEATURE_CORRELATOR |
| nevisDetect Persistency | DETECT_PERSISTENCY |
| nevisDetect Controller | DETECT_CONTROLLER |
See how in the default role-permission-mapping a security role is mapped onto permissions:
Security role: DETECT_FORENSIC_EXPERT
APP_MANAGEMENT_READAPP_MANAGEMENT_PLUGIN_WRITEAPP_MANAGEMENT_GLOBAL_WRITEAPP_MANAGEMENT_FILTER_WRITEAPP_MONITORING_READCASE_OVERVIEW_READCASE_WRITECID_READGENERATED_RULES_READGENERATED_RULE_TOGGLE_ACTIVEGENERATED RULE_WRITEPLUGIN_OVERVIEW_READPLUGIN_RISK_SCORE_WRITEPOLICY_OVERVIEW_READPOLICY_TOGGLE_ACTIVEPOLICY_WRITEPOLICY_CREATEREFDATA_READRISK_SCORE_NORMALIZATION_CALCULATERISK_SCORE_NORMALIZATION_READUSER_OVERVIEW_READ
Security role: DETECT_SECURITY_OFFICER
APP_MANAGEMENT_READAPP_MANAGEMENT_PLUGIN_WRITEAPP_MANAGEMENT_GLOBAL_WRITEAPP_MANAGEMENT_FILTER_WRITEAPP_MONITORING_READCASE_OVERVIEW_READCASE_WRITEGENERATED_RULES_READGENERATED_RULE_TOGGLE_ACTIVEGENERATED_RULE_WRITEPLUGIN_OVERVIEW_READPLUGIN_RISK_SCORE_WRITEPOLICY_OVERVIEW_READPOLICY_TOGGLE_ACTIVEPOLICY_WRITEPOLICY_CREATEREFDATA_READRISK_SCORE_NORMALIZATION_CALCULATERISK_SCORE_NORMALIZATION_READUSER_OVERVIEW_READ
Security role: DETECT_OPERATOR
APP_MANAGEMENT_READAPP_MANAGEMENT_PLUGIN_WRITEAPP_MONITORING_READPLUGIN_OVERVIEW_READREFDATA_READRISK_SCORE_NORMALIZATION_READ
Security role: DETECT_HELPDESK
CASE_OVERVIEW_READCASE_WRITEGENERATED_RULES_READGENERATED_RULE_TOGGLE_ACTIVEPLUGIN_OVERVIEW_READPOLICY_OVERVIEW_READREFDATA_READRISK_SCORE_NORMALIZATION_READUSER_OVERVIEW_READCID_READ
For a complete overview of the existing permissions and the default mapping, see Appendix: Role to Permission Mapping.
One security role can be mapped onto several permissions.
Authentication
nevisProxy and nevisAuth take care of the user authentication and the assignment of the security roles:
- They include the identity of the user as well as his security roles in the Nevis SecToken and forward the token to nevisDetect.
- nevisDetect authenticates the user by verifying the signature of the SecToken.
The authentication of a nevisDetect component happens during the 2-way TLS handshake:
- The calling component sends its X509 certificate during the TLS handshake.
- The called component ensures that the X509 certificate is issued by a known and trusted Certificate Authority.
Authorization
The authorization process includes three steps:
- First, the system retrieves the security roles of the caller.
- In the case of a user, the security roles are retrieved from the SecToken.
- In the case of a nevisDetect component, a single security role is derived from the Subject of the X509 certificate. For this, it is possible to configure a regular expression. The default regular expression extracts the Common Name (CN) from the Subject of the X509 certificate.
- As a next step, the system retrieves the permissions of the caller based on its security role.
- Finally, the system ensures that the caller has the requested permission for the service.