Authorization
An authorization is a mapping or an assignment of a role to a profile. If the role is a nevisIDM role, the following attributes further define the exact character of the authorization:
- Application data room: The application for which the user is authorized to exert the assigned nevisIDM role.
- Unit data room: The units for which the user is authorized to exert the assigned nevisIDM role. Being authorized for a unit includes being authorized for its subunits and the users contained within those units.
- Client data room: The client (tenant) for which the user is authorized to exert the assigned nevisIDM role. It is only viewable in multi-client mode.
- Enterprise role data room: The enterprise roles for which the user is authorized to exert the assigned nevisIDM role. This data room is only available if the enterprise role feature is enabled per global config flag.
An authorization may be valid for a data room holding more than one application, unit, client, or enterprise role. And it is even possible to define that the authorization is responsible for all applications (application-global), for all units (unit-global), for all clients (client-global), or all enterprise roles (enterpriserole-global).
Client-global or authorizations involving more than one client are very extensive authorizations. In practice, only root administrators should be given such vast privileges.
The figure below shows some examples of application and unit data rooms. An in-depth discussion of the subject can be found in the chapter: Security. The figure does not show the client data room which has to be understood as superior data room of the unit and application data room. I.e., a certain unit data room can only be assigned to a user if the user is authorized for the client data room of the client the unit belongs to.
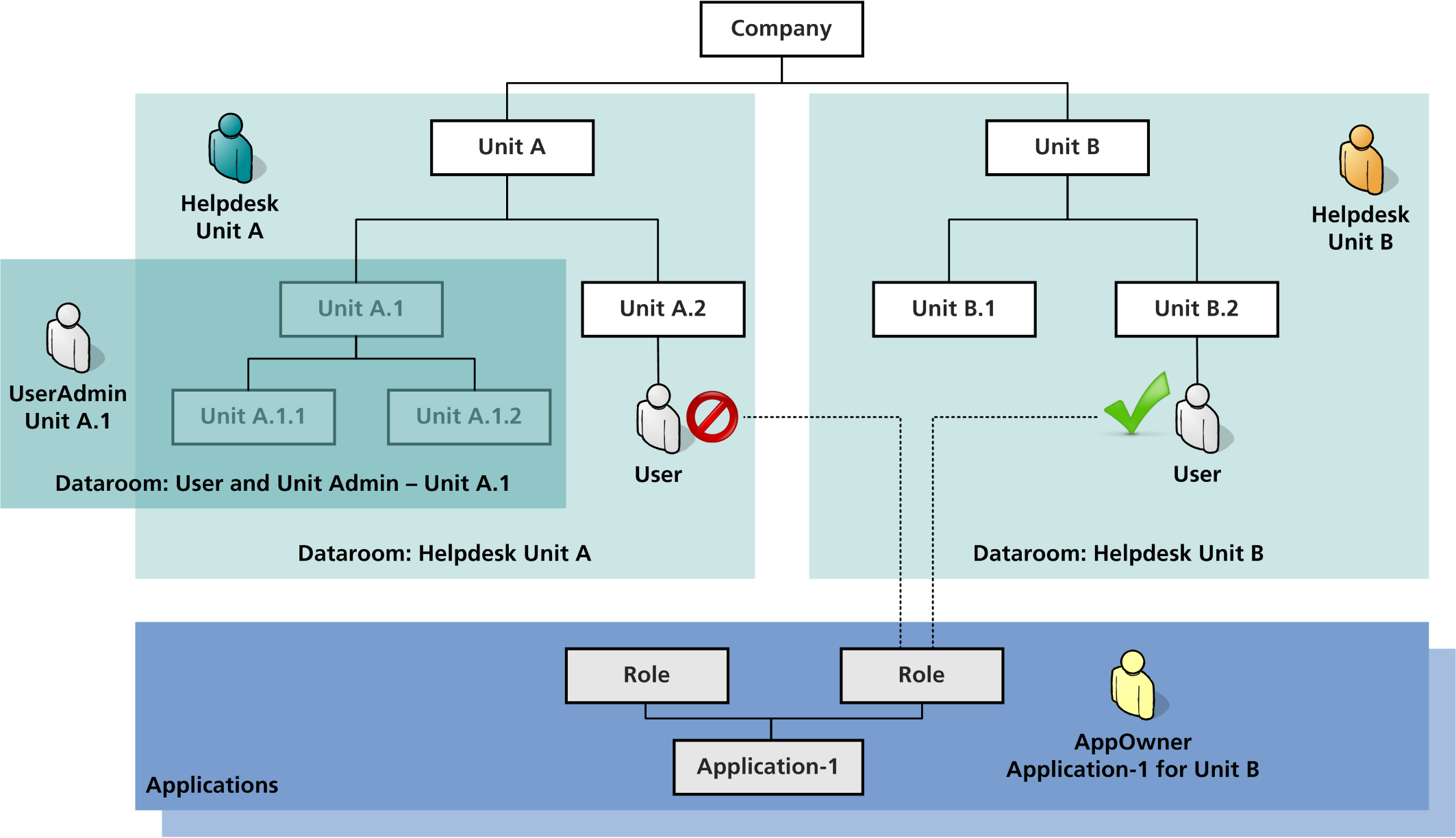
Fig. 1: Hierarchically structured units within nevisIDM
Database table TIDMA_AUTHORIZATION
| DB attribute | Java data type (max. size), defaults | Description |
|---|---|---|
| appl_global | Boolean, not NULL | Defines if the authorization is application-global, i.e., not restricted to certain applications. |
| authorization_id | Long, not NULL | Primary key (uniquely identifies each individual DB entry) |
| client_global | Boolean, not NULL | Defines if the authorization is client-global, i.e., not restricted to certain clients. |
| erole_global | Boolean, not NULL | Defines if the authorization is enterprise-role-global, i.e., not restricted to certain enterprise roles. |
| profile_id | Long, not NULL | Defines the profile the authorization belongs to. Foreign key that links to information in the table TIDMA_PROFILE. |
| role_id | Long, not NULL | Defines the role the authorization belongs to. Foreign key that links to information in the table TIDMA_ROLE. |
| unit_global | Boolean, not NULL | Defines if the authorization is unit-global, i.e., not restricted to certain units. |
| valid_from | Date, nullable | The authorization is valid from the valid_from date onward. If this date is in the future, the authorization is not assigned on login nor populated in, for example, the SecToken. The "Null" value means no restriction. |
| valid_to | Date, nullable | The authorization is valid until the valid_to date. If this date is in the past, the authorization is not assigned on login nor populated in, for example, the SecToken. The "Null" value means no restriction. |
Database table TIDMA_AUTHORIZATION_APPL
In this table, the mappings between authorizations and applications are stored. These mappings define the restrictions of an authorization to a certain set of applications, the "application data room".
| DB attribute | Java data type (max. size), defaults | Description |
|---|---|---|
| application_id | Long, not NULL | Foreign key that links to information in the table TIDMA_APPLICATION. |
| authorization_appl_id | Long, not NULL | Primary key (uniquely identifies each individual DB entry) |
| authorization_id | Long, not NULL | Foreign key that links to information in the table TIDMA_AUTHORIZATION. |
Database table TIDMA_AUTHORIZATION_UNIT
In this table, the mappings between authorizations and units are stored. These mappings define the restrictions of an authorization to a certain set of units, the "unit data room".
| DB attribute | Java data type (max. size), defaults | Description |
|---|---|---|
| authorization_id | Long, not NULL | Foreign key that links to information in the table TIDMA_AUTHORIZATION. |
| authorization_unit_id | Long, not NULL | Primary key (uniquely identifies each in |
| unit_id | Long, not NULL | Foreign key that links to information in the table TIDMA_UNIT. |
Database table TIDMA_AUTHORIZATION_CLIENT
In this table, the mappings between authorizations and clients are stored. These mappings define the restrictions of an authorization to a certain set of clients, the "client data room".
| DB attribute | Java data type (max. size), defaults | Description |
|---|---|---|
| authorization_client_id | Long, not NULL | Primary key (uniquely identifies each individual DB entry) |
| authorization_id | Long, not NULL | Foreign key that links to information in the table TIDMA_AUTHORIZATION. |
| client_id | Long, not NULL | Foreign key that links to information in the table TIDMA_CLIENT. |
Database table TIDMA_AUTHORIZATION_EROLE
In this table, the mappings between authorizations and enterprise roles are stored. These mappings define the restrictions of an authorization to a certain set of enterprise roles, the "enterprise role data room".
| DB attribute | Java data type (max. size), defaults | Description |
|---|---|---|
| authorization_erole_id | Long, not NULL | Primary key (uniquely identifies each individual DB entry) |
| authorization_id | Long, not NULL | Foreign key that links to information in the table TIDMA_AUTHORIZATION |
| enterprise_role_id | Long, not NULL | Foreign key that links to information in the table TIDMA_ENTERPRISE_ROLE |