System Settings
System Settings provide users with direct access to modify the core, underlying configurations of your Authentication Cloud instance. This function allows you to fine-tune the service to precisely meet your operational and security requirements.
These settings control critical functions of your Authentication Cloud Instance. Modifying System Settings incorrectly can lead to service instability, unexpected behaviour, and potential service interruptions. We strongly recommend that only technical users with a full understanding of the consequences make any changes.
General
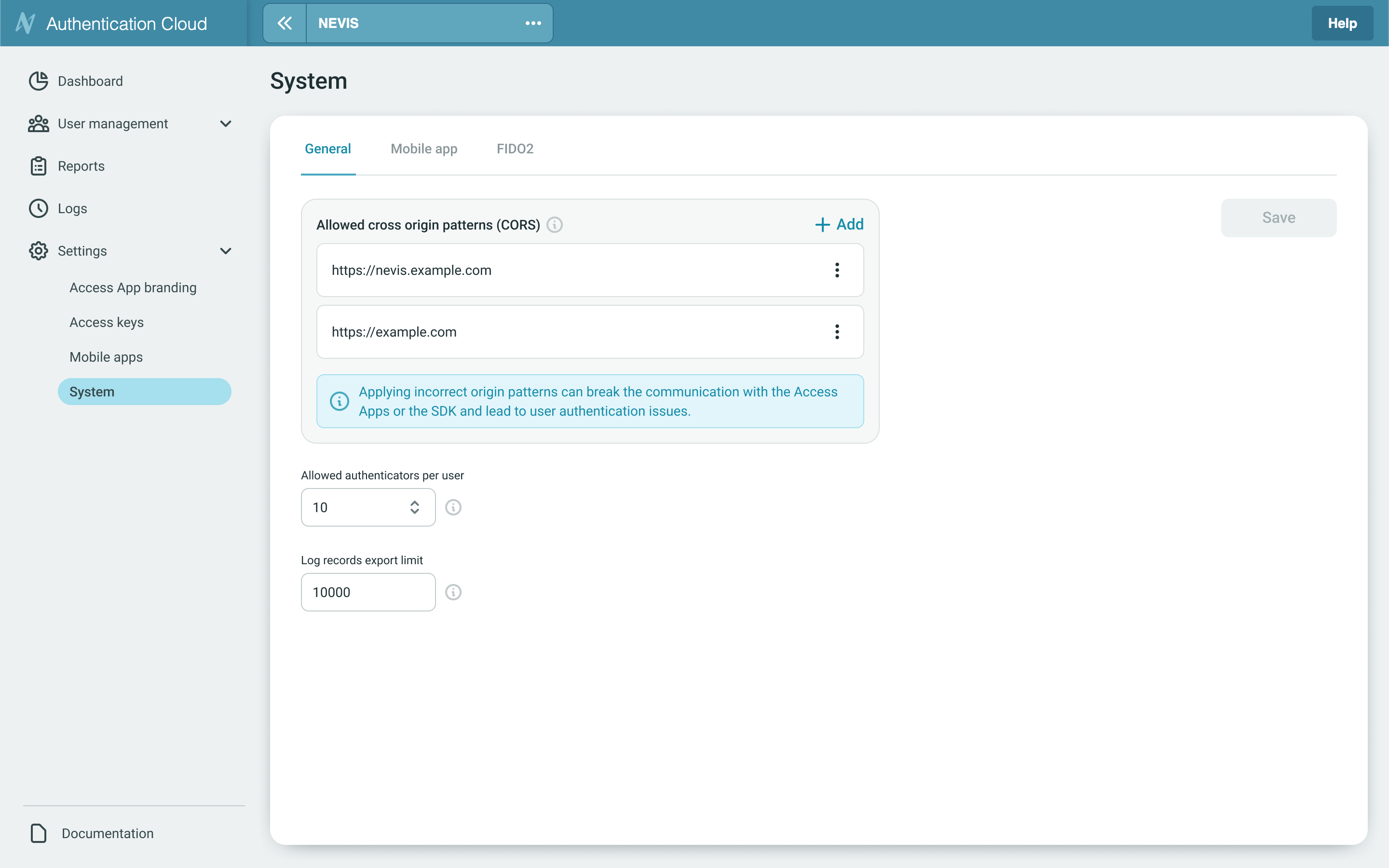
Allowed Cross-Origin Patterns (CORS)
Cross-Origin Resource Sharing (CORS) settings define which external web origins (domains) are allowed to communicate with your authentication service. Correctly configuring these origins ensures that trusted applications can securely interact with the system.
Configuration
- Click the ➕ Add button.
- Enter the full origin URL. Example value: https://example.eu/
- Save the configuration.
- To delete or edit an existing origin: use the ⋮ (options menu) next to the entry.
Allowed Authenticators per User
Defines the maximum number of authenticators (e.g., devices, tokens, or apps) that a single user can register. Default maximum value is 10. Leave empty for no limit.
Log records export limit
Determines the maximum number of log records (multiple of 250) that can be exported in a single request.
Mobile
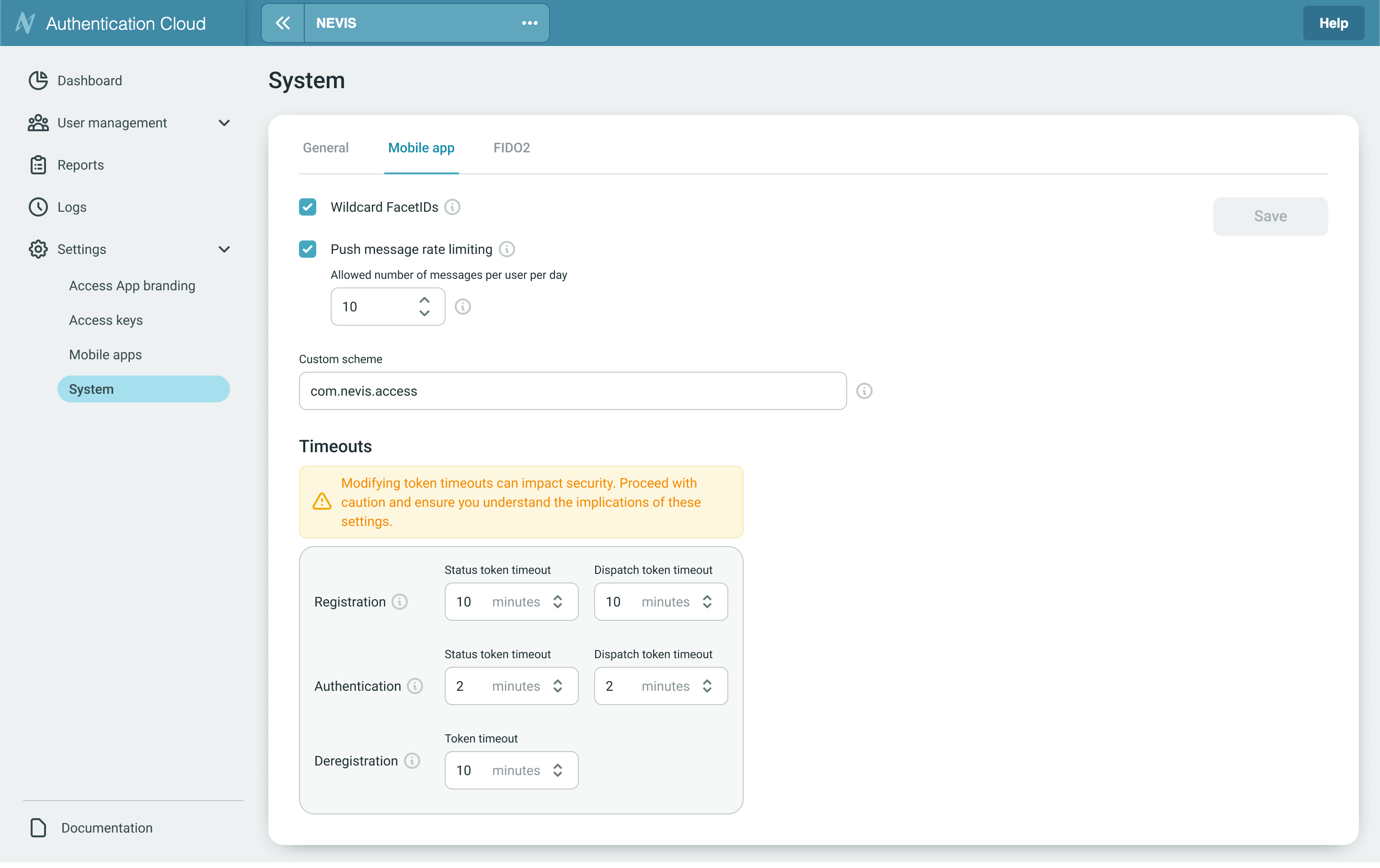
Wildcard FacetIDs
Activating Wildcard Facet IDs allows your backend to support any client facet ID, which significantly accelerates application development and initial testing. This setting bypasses security checks and must not be enabled for production SDKs.
Push message rate limiting
Push message rate limiting is a defence designed to defeat malicious actors by preventing them from flooding a user's device. It enforces a strict limit on the volume of push requests that can be sent to a user within a rolling 24-hour period, safeguarding system stability.
Custom scheme
Custom URI scheme of your mobile application for deep links (e.g., 'companyapp'). Leave empty to use standard HTTPS-based app links.
Timeouts
This section allows administrators to configure token timeout values used during registration, authentication, and deregistration workflows. Token timeouts define how long a token remains valid before expiring.
Modifying token timeouts can impact security. Proceed with caution and ensure you understand the implications of these settings.
Registration Timeouts
Tokens generated during user registration determine how long a registration session remains valid. The user has to restart the registration if they cannot finish it before the timeout.
- Status Token Timeout : Defines how long the status token remains valid for tracking registration progress.
- Dispatch Token Timeout: Defines how long a dispatched token remains valid for completing the registration process.
Authentication Timeouts
Tokens used during authentication sessions define how long a login attempt remains valid. The user has to restart the authentication if they cannot finish it before the timeout.
- Status Token Timeout: Determines how long the system will wait for authentication status updates.
- Dispatch Token Timeout: Defines how long an authentication request token remains valid for completing login.
Deregistration Timeout
The timeframe available for the client to redeem the deregistration token, from the moment the token has been generated.
- Token Timeout: Provides a secure window for completing deregistration.
FIDO2
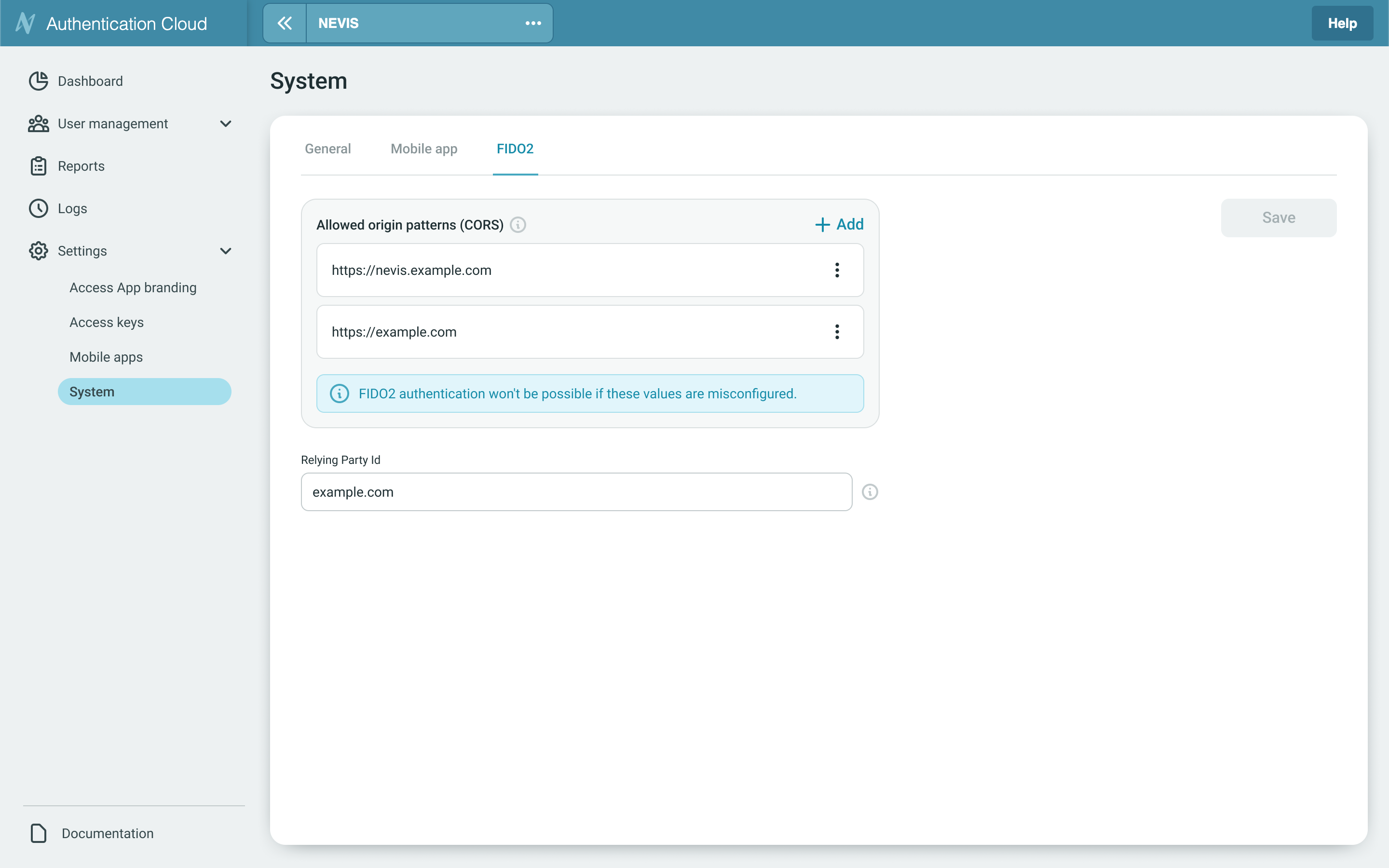
Relying Origin
This is the specific Origin URL of your web application from which authentication requests will be initiated. It acts as the authorized host where your users will securely complete the authentication process.
Configuration
- Click the ➕ Add button.
- Enter the full origin URL. Example value: https://example.eu/
- Save the configuration.
- To delete or edit an existing origin: use the ⋮ (options menu) next to the entry.
FIDO2 authentication won't be possible if these values are misconfigured.
Relying Party Id
This is a unique identifier that defines the scope of all credentials created for your service. It is typically set to your domain name (e.g., example.com), ensuring that credentials registered on one subdomain can be used across all other related subdomains. There can only be a single domain associated with an instance.