Mobile authentication basics
As passwords are no longer considered secure enough, businesses are increasingly using mobile authentication to protect their users and services. Mobile authentication software uses the security chip and the built-in authentication capabilities of the mobile device to ensure that the person who wants to sign in to the service is the owner who originally signed up.
During signup, customers use their device with the mobile authentication app to register their account. This creates a pair of cryptographic keys, a private key that remains on the phone and a public key that is transferred to the server side.
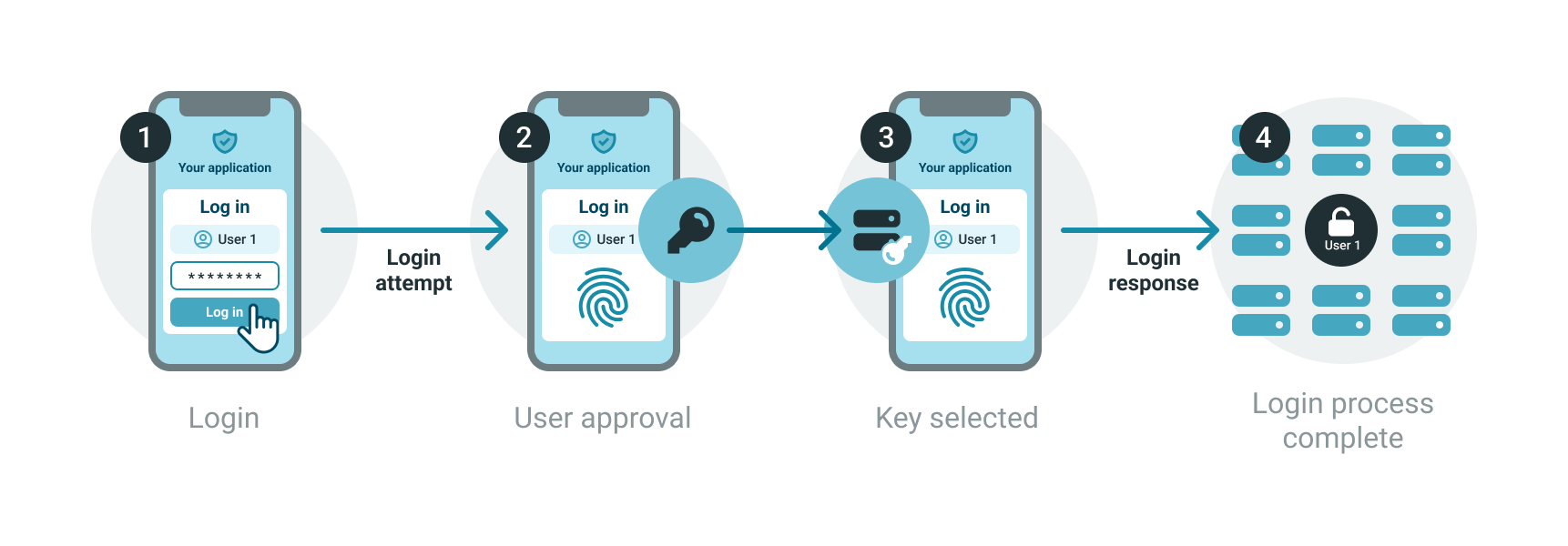
Later on, when users want to sign in again, the authenticator uses a biometric recognition method to identify and authenticate them, sending a session signature that was signed with the private key and whose validity can be checked using the corresponding public key. Transactions can be signed in a similar manner.