QR codes
QR codes can be used to register users and authenticators, but also as a secure and versatile transaction authentication method.
QR codes overview
QR code based transaction approval is one of the most reliable authentication methods as it does not rely on communication with a specific device. This makes it ideal in cases where more convenient mechanisms, such as push notifications are not acceptable.
We recommend QR codes as an authentication method, if the following are true for your business:
- You want secure authentication to work with the widest range of devices.
- You do not want to rely on the availability of push services on user devices.
- You want the option for usernameless authentication.
- You do not want to invest in major technical development.
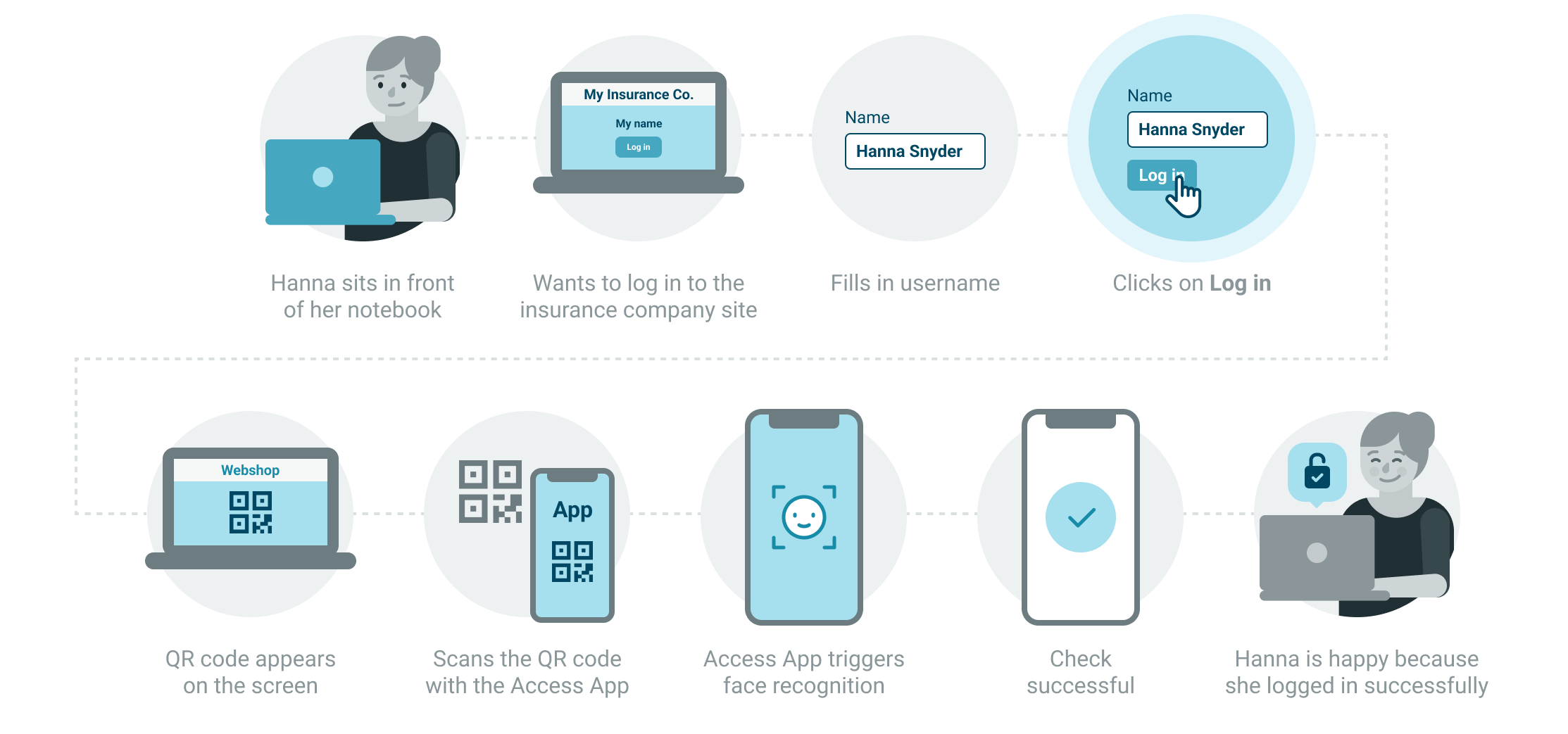
For authentication with QR codes, you do not rely on specific device capabilities, or settings on the user side. Your users can register any Android or iOS device as an authenticator, and use them to authenticate transactions.
When the web application calls for authentication, it presents a QR code. Users scan the QR code using the mobile app on one of their registered authenticator devices, and sign the transaction with either a PIN, or biometrics.
QR code based requests, like push messages, can also be fetched directly from a user device. For more information, see Fetch ongoing operations
Registration and authentication flow
To get started, you need the following information available:
- Instance ID
- Access Key
For more information on the instance ID and the Access Key, see the API documentation.
To implement and use QR codes, see the instructions on the following pages:
For more information about usernameless transaction approval, and how it can be implemented using QR codes, see Usernameless authentication.
Read more about QR codes in the QR Code section of the Access App documentation.