Adaptive authentication
When implementing authentication, businesses often have to choose between security and user convenience. Either they can implement highly secure, high-friction multi-factor authentication flows or go for a low-friction, low-security login scenario. With adaptive authentication, you no longer have to decide between security and user convenience, as you can dynamically react during login flows, depending on underlying contextual information or business rules. For more details please visit and read our blog post: What Is Adaptive Authentication.
Adaptive authentication effectively balances your security requirements with the optimal user experience. During login, Nevis automatically collects, parses and assesses various signals from the current users' context.
For example:
- Their current location (geo-location).
- Their traveling distance (geo-velocity), if they did sign-in previously from other locations.
- Their device, with advanced fingerprinting.
- Their intended action.
- Their source IP reputation, based on external IP reputation services.
Based on these various inputs for each authentication, Nevis continuously builds a risk profile for the user. Nevis reacts to specific events and risk scenarios, such as sign-in from a new device or an impossible travel (e.g. a sign in within hours from both Berlin and San Francisco) and can decide to notify the user or provide additional means of authentication via multi factor authentication. You can read here for more technical details.
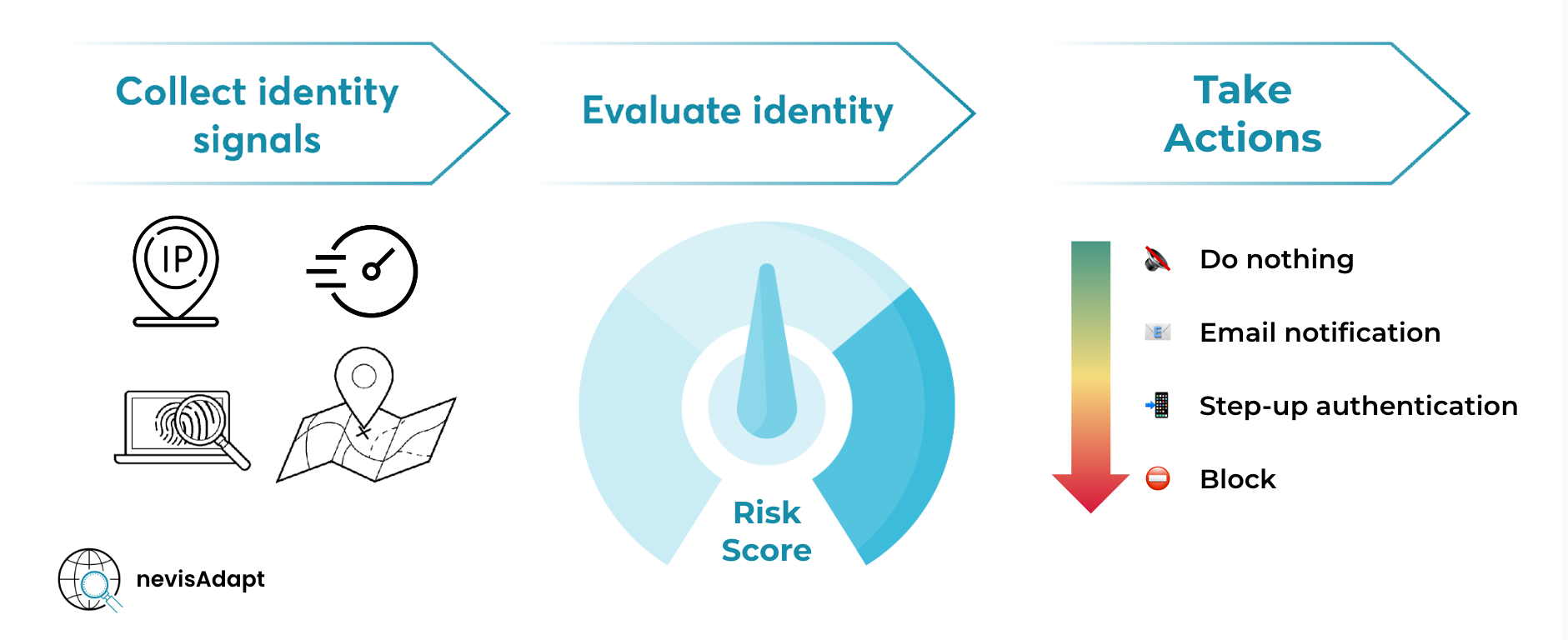
With Nevis you have the freedom and power to fully configure your adaptive risk engine. You can decide which of the contextual signals the risk engine should take into consideration, how these signals should be weighed, what the thresholds should be, and what actions should be triggered if an authentication attempt is flagged as risky.
React with Risk Profiles
With the risk profiles one can have strict or balanced options, with pre-configured medium and high threshold values. These values could be fine-tuned by the user if needed. The profiles have been designed in a way to react as described in the table nested bellow. We can provide further fine-tuning if needed in case of special client circumstances.
Typical use cases and the associated expected behavior
| ID | Case | Use Case | Strict risk level | Balanced risk level |
|---|---|---|---|---|
| 1 | Move an established device to a new country (not black listed) | Traveling from HU to CH with my phone. | MED | LOW |
| 2 | Move an established device to a new country (black listed) | Traveling from HU to a blacklisted country with my phone. | HIGH | MED |
| 3 | Move a known device to a new country (not black listed) | Traveling from HU to CH with a device I used only once before. | MED | LOW |
| 4 | Move a known device to a new country (black listed) | Traveling from HU to Pakistan with the a device I used only once before. | HIGH | MED |
| 6 | Modify your browser significantly (known device - unknown fingerprint) | Changed screen resolution on family PC. | LOW | LOW |
| 7b | Change browser (unknown device - established+unique fingerprint - unique IP) (in your established country) | New browser on my personal laptop. | HIGH | MED |
| 5 | Change browser (unknown device - established+unique fingerprint - shared IP) (in your established country) | Taking my personal laptop to the workplace and signing in through a different browser. | HIGH | MED |
| 7 | Change browser (unknown device - established+shared fingerprint - unique IP) (in your established country) | Taken my workplace notebook to home and started a different browser. | HIGH | MED |
| 7c | Change browser (unknown device - established+shared fingerprint - shared IP) (in your established country) | Singing in on my coworker's similar laptop at work but using a different browser. | HIGH | MED |
| 8 | Change browser (unknown device - established+unique fingerprint) (in a new country) | Taking my laptop to Switzerland for the first time and singing in from a different browser. | HIGH | HIGH |
| 8b | Change browser (unknown device - established+unique fingerprint + new IP) (established country) | Taking my laptop to my friend's house for the first time and signing in to a new browser. | HIGH | HIGH |
| 9 | Signing in from a public hotspot (established device, unknown + probably shared IP + unknown country) | Signing in from a never visited airport on my phone. | LOW | LOW |
| 10+12 | Signing in from a public hotspot (established device, unknown + probably shared IP + established country) | Signing in from the railway WIFI in Hungary. | LOW | LOW |
| 13 | Signing in from a public hotspot (unknown + probably shared IP + established Location) + new device (case 5) | Signing in with a new device on the railway WIFI in Hungary. | HIGH | HIGH |
| 11 | Signing in from a public computer | Using a new computer in a lab. | HIGH | HIGH |
| 11b | Signing in from an established family shared computer | LOW | LOW | |
| 11c | Signing in from from a family shared computer for the second time (first time will trigger the same as a new device) | MED | LOW | |
| 14 | Same device, same finger, only new IP, established location | Reconfiguring my router at home / ISP assigns a new IP to me. | LOW | LOW |
| 11 | Signing in from a public computer (new device, new IP, new fingerprint) (In established country) | Signing in in a printing shop to my account to print something in Hungary. | HIGH | HIGH |
| 15 | Singing in from your new computer at home (new device, established IP, new fingerprint) (In established country) | Using my new laptop at home. | HIGH | HIGH |
| 16-17 | Signing in from your new computer at home but same model (new device, established IP, assuming established+shared fingerprint) (In established country) | Having the same model of replacement laptop at home or at work. | HIGH | MED |
| 18 | Signing in from your new computer at a new location but same model (new device, established IP, assuming established+shared fingerprint + new+shared IP) (In established country) | Having the same model of replacement laptop in a new country. | HIGH | HIGH |
| 20 | Your existing IP finds its way into the black list (but you are still using an established environment) | LOW | LOW | |
| 23 | IP velocity trigger | You seem to login from an IP that is located a long distance away in a short amount of time. | HIGH | MED |
| 23b | Same as 23 but you end up in the same country | MED | LOW | |
| 24 | IP reputation trigger | Your new IP has a bad reputation score and appears to come from another country. | HIGH | MED |
| 24b | Same as 24 but the IP seems to be in the same country | MED | LOW | |
| 25-27 | Evilginx detection | HIGH | HIGH |
React to Events
Besides the sophisticated and advanced risk profiling of Nevis which can be fine-tuned down to the smallest detail for your specific use cases, we have also developed a simpler to configure, but nonetheless, highly-effective, rule-based risk engine.
Simply choose from pre-defined events and decide on the desired behavior that should be triggered with “if-then” rules and you are good to go.
The project template
The Nevis project template Adaptive Authentication is configured to use the nevisIDM Admin GUI application by default as the protected web service. It supports username / password login infrastructure as first authentication step and further, additional security elements (silent e-mail notification, step-up authentication) according to the risk evaluation results. This is subject to change by the user.
For demonstration purposes, the template also includes a demo application called adaptapp (showcasing the reporting REST API of nevisAdapt) that helps to overview login and session details.
Scenario for testing a successful deployment
- Launch your nevisIDM Administration GUI application at
https://your_domain_goes_here/nevisidm- replace “your_domain_goes_here” with your real domain name! - Login with your default bootstrap credentials (and change your initial password).
- At first login (so called training mode) a second factor authentication is required (email TAN → default, hardcoded/test code is AAAAA). In case of success login is granted → nevisIDM Admin GUI appears
- Logout!
- Perform a second login without changing environment (browser, user, IP, etc) → NO second factor authentication is required since the connection is already a known one, login is granted → nevisIDM Admin GUI appears
- Now it is time to replace the exposed example application by your own service and enjoy the Nevis security experience!