Setting Up a SAML Identity Provider
Preconditions
You need a Realm pattern that defines the process for initial authentication. See Configuring LDAP Login for Web Application for an example configuration.
To use the IDP, you have to integrate at least one SP. You need the following information about the SP:
- The signer certificate
- The SP issuer
- The Assertion Consumer Service URL (used for IDP-initiated authentication only)
Realm Patterns
You can add a new Realm pattern, or reuse an existing Realm pattern. The SAML IDP pattern just exposes the realm as an authentication service via nevisProxy.
If you add a new pattern, you can pick any kind of Realm pattern. The Authentication Realm is usually the most convenient choice because it offers many standardized configuration options.
Quick Start
Perform the next steps to set up a SAML IDP.
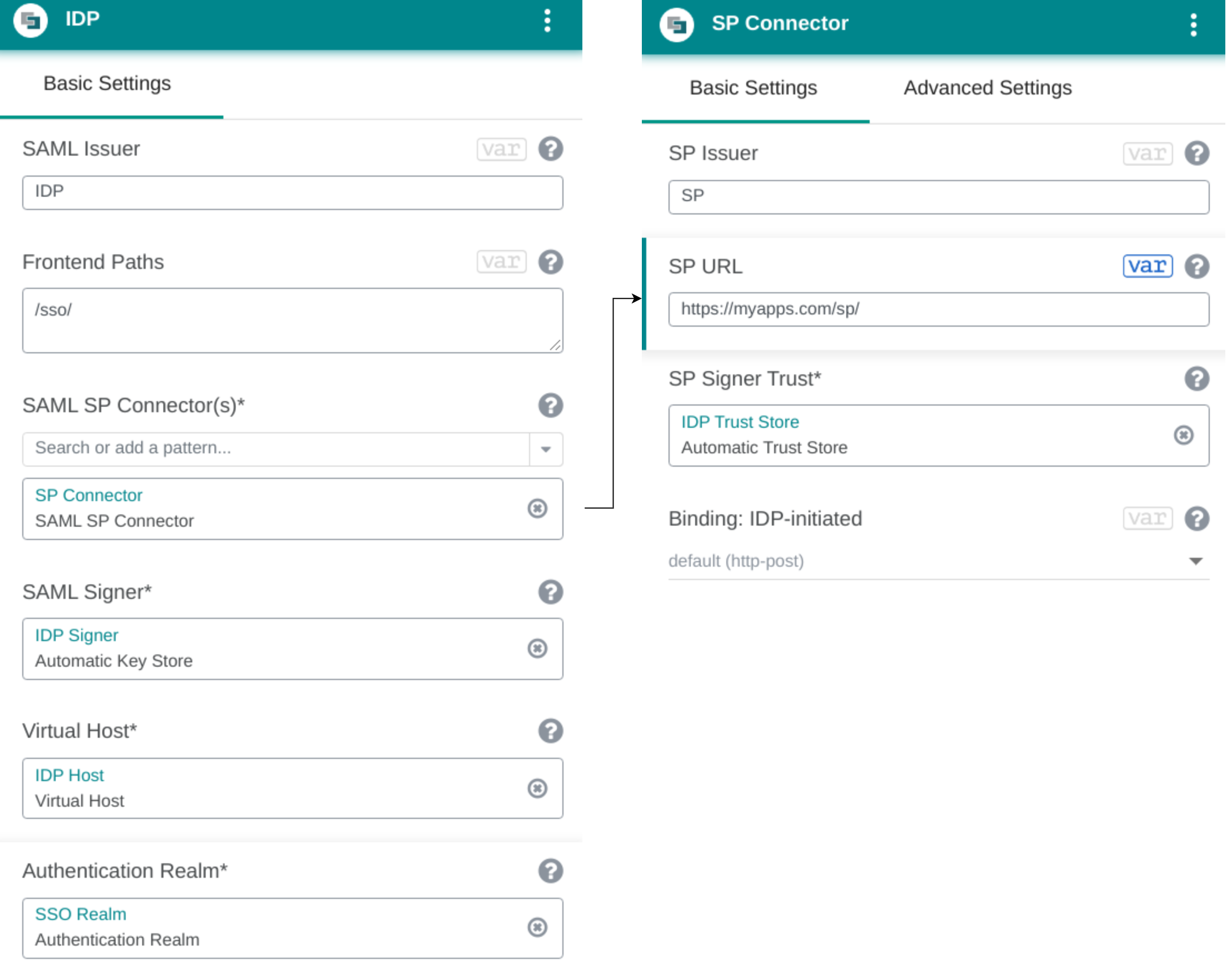
- Configure the SAML IDP pattern as follows:
- Enter a value for the SAML issuer in the SAML Issuer field.
- The SP needs this information to validate SAML responses.
- Some SPs require the issuer to be a URL that points to the IDP.
- Enter at least one frontend path in the Frontend Paths field, or use the default.
- Assign a SAML SP Connector pattern to the SAML SP Connector(s) field.
- Configure the SAML signer in the SAML Signer field, by assigning an (Automatic) Key Store pattern.
- Assign a Virtual Host pattern to the Virtual Host field. The assigned Virtual Host pattern defines where to make the frontend path accessible.
- In the Authentication Realm field, specify an Authentication Realm pattern that provides the authentication flow.
- Enter a value for the SAML issuer in the SAML Issuer field.
- Configure the SAML SP Connector pattern as follows:
- Enter the SP issuer in the SP Issuer field.
- Establish SP signer trust by assigning a truststore provider pattern, such as an Automatic Trust Store pattern, to the SP Signer Trust field.
Describes how to configure the SAML SP Connector pattern. You can also have a look at the pattern on the right in the next figure.
Automatic Key Management
For test setups and in case the SP is defined in the same nevisAdmin 4 project, you can use automatic key management. Proceed as follows:
- Assign an Automatic Trust Store pattern to the SP Signer Trust field of the SAML SP Connector pattern.
- Link the Automatic Trust Store pattern with the automatic keystore used by the SP, by assigning the relevant Automatic Key Store pattern to the Trusted Key Stores field of the Automatic Trust Store pattern.
For production setups, either use the nevisKeybox Store pattern, or the PEM Trust Store / PEM Key Store provider patterns.
IDP-initiated Authentication
The SP URL property of the SAML SP Connector pattern is required for IDP-initiated authentication.
IDP-initiated authentication will be supported in a future release.
The following figure shows a sample configuration for both patterns:
Integrating multiple SPs
If you want to integrate multiple SPs, configure one SAML SP Connector pattern for each SP that you want to integrate. Attach all the SAML SP Connector patterns to the SAML SP Connector field of the SAML IDP pattern.
Implementation Notes
nevisAdmin 4 will add an own IdentityProviderState AuthState for each SAML SP Connector to the esauth4.xml file of nevisAuth. The system will select the correct IdentityProviderState based on the Issuer of the incoming AuthnRequest SAML request.