OIDC Token Authorization Code Flow - PKCE
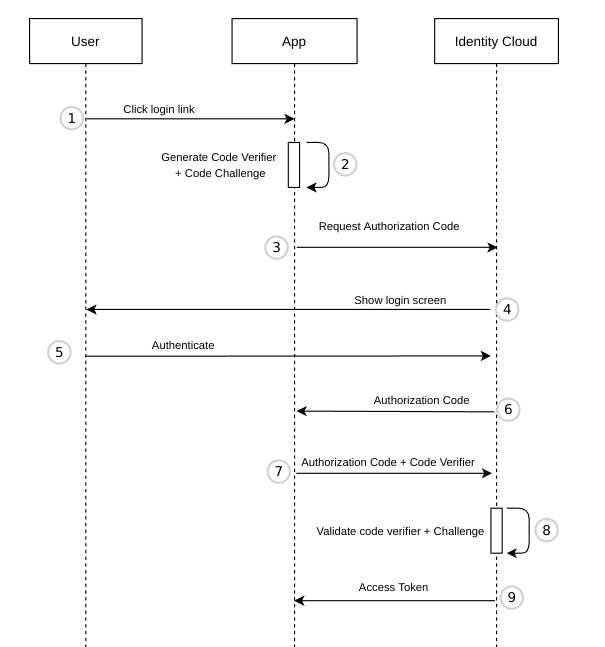
- The user clicks Login in the App.
- The App has to provide 2 codes for PKCE:
code_verifier- must be a randomStringand at least 43 characters long.code_challenge- URL-safe base64 encoded SHA256 hash of the code_verifier. The codes ensure message integrity. Even if an attacker intercepts the Authorization Code, they won't be able to obtain an Access Token as they also need thecode_verifierand thecode_challenge
- The App redirects the user to the Identity Suite Authorization endpoint.
- Identity Suite shows a login page.
- The user authenticates by entering their credentials.
- Upon successful authentication, the authorization endpoint stores the code challenge, generates an _Authorization Code, and redirects the user to the return_uri. The code is added as a query parameter.
- The App sends the Authorization Code to the Identity Suite Token endpoint, together with the code_verifier (from step 2).
- The token endpoint verifies the code_challenge and the code_verifier (received in step 2).
- The token endpoint returns an Access Token. Depending on the scopes requested additional tokens will be returned:
- ID Token: scope
openid - Refresh Token: scope
offline_access
- ID Token: scope
For more information see the Authorization Code with PKCE chapter of the Identity Suite documentation.
Example JSON response:
{
"access_token":"...",
"refresh_token":"...",
"id_token":"...",
"token_type":"Bearer",
"expires_in":3600
}