Configuring SAML Authentication for a Web Application
Preconditions
- Make your application accessible via nevisProxy as explained in Protecting a Web Application.
- Make sure you have the following information about your IDP at hand:
Supported IDPs
You can integrate a third-party SAML Identity Provider ".
Quick Start
Authentication via SAML (Web Browser SSO) requires:
- The configuration of a SAML Service Provider (SP).
- The integration of the SP with the IDP.
Perform the next steps:
In the relevant Web Application pattern:
Attach a SAML SP Realm pattern to the Authentication Realm field. See the next step for more information on how to configure the SAML SP Realm pattern.
To configure the SAML SP Realm pattern:
Go to the nevisAuth Connection tab and attach a nevisAuth Instance pattern to the nevisAuth field.
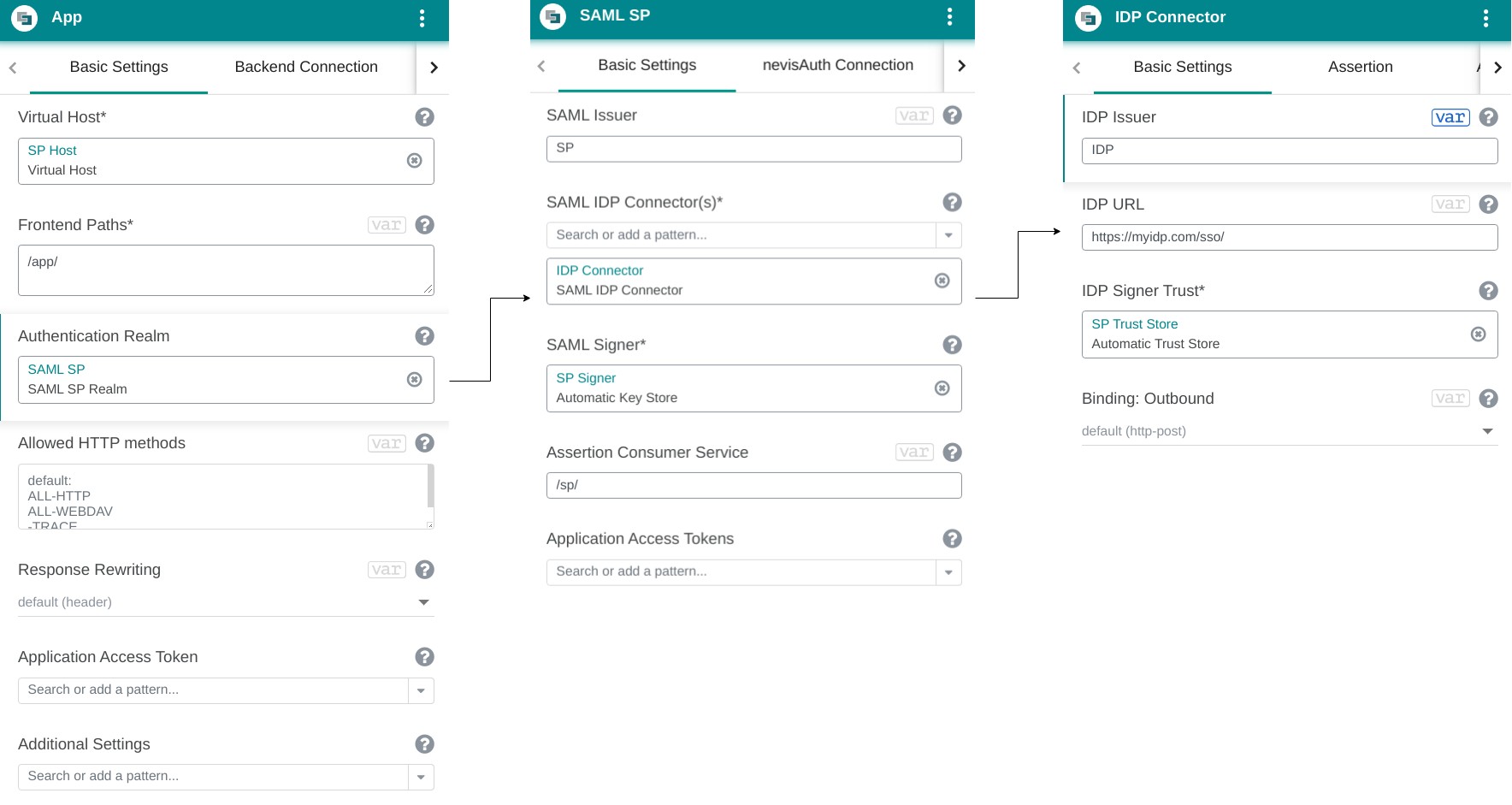
Open the Basic Settings tab and make the following configurations:
Enter an arbitrary value for the SAML issuer in the SAML Issuer field. Inform your IDP about the value you have chosen.
Assign a Key Store pattern to the SAML Signer (field). By specifying the keystore, you define which key material to use for signing the outgoing SAML messages.
Assign a SAML IDP Connector pattern to the SAML IDP Connector(s) field. See the next step for more information on how to configure the SAML IDP Connector pattern.
To configure the SAML IDP Connector pattern:
Enter the IDP Issuer in the IDP Issuer field.
To find out the correct value of the IDP Issuer, either check the metadata of the IDP, or base64-decode a received SAML Response.
Enter the URL of the IDP in the IDP URL field.
The SP may invoke the authentication process by sending an AuthnRequest SAML message to this URL.
Assign a relevant truststore pattern to the IDP Signer Trust field.
Depending on the type of truststore pattern, you have to do additional configuration.
Automatic Key Management
For testing purposes and if the IDP is configured in the same nevisAdmin 4 project, you can use automatic key management. Proceed as follows:
- SAML SP Realm pattern: Assign an Automatic Key Store pattern to the SAML Signer field.
- SAML IDP Connector pattern: Assign anAutomatic Trust Store pattern to the IDP Signer Trust field.
- Automatic Trust Store pattern: Enter the Automatic Key Store pattern used by the IDP in the Trusted Key Stores field.
For production setups, either use the nevisKeybox Store pattern, or the PEM Trust Store / PEM Key Store provider patterns.
The following figure shows a sample configuration for all patterns involved:
Session Upgrade
For SP-initiated authentication, the SP sends a SAML AuthnRequest to the IDP. This AuthnRequest contains the following element:
<samlp:RequestedAuthnContext>
<saml:AuthnContextClassRef>urn:nevis:level:1</saml:AuthnContextClassRef>
</samlp:RequestedAuthnContext>
This RequestedAuthnContext element defines the minimum required authentication level. If you want to demand a higher authentication level, you can assign an Authorization Policy to your application. When the session is not at this level yet, the SP will send an additional AuthnRequest to the IDP.
Customize AuthnContext
The value of AuthnContext is not standard and may lead to issues when your SP is integrated with a third-party IDP. To solve these issues, you can remove the AuthnContext or replace its value, in the Custom Properties field of the SAML IDP Connector pattern (Advanced Settings tab). See the Help on the right side of the nevisAdmin 4 screen for details.
Integrating Multiple IDPs
It is possible to assign multiple SAML IDP Connector patterns to a single SAML SP Realm pattern.
When authentication is requested, the system selects the correct IDP by evaluating a nevisAuth expression. You define this expression in the Selection Expression field of a SAML IDP Connector pattern (Advanced Settings tab). The expression must evaluate to "true" for exactly one IDP.
Selection of the IDP by the user is not yet supported.