Virus protection using ClamAV
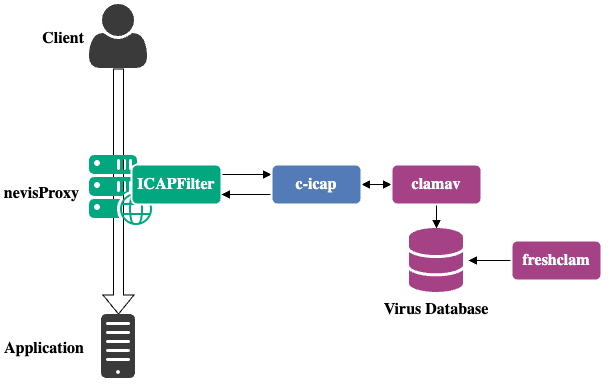
The nevisAppliance includes the Clam antivirus scanning engine which can be used by nevisProxy to detect and block HTTP requests/responses containing a virus.
For virus protection with ClamAV to work on the nevisAppliance, first manually download and then constantly update the virus signature database. See Update the virus signature database for instructions.
Configure and start c-icap daemon
nevisProxy forwards HTTP requests/responses via the ICAP protocol to the ClamAV daemon. The c-icap daemon is used to implement this interface.
The following tasks are necessary to start the c-icap server:
Copy the configuration template:
cp /usr/local/c-icap/etc/c-icap.conf.tmpl \
/usr/local/c-icap/etc/c-icap.confOptional: You may now want to adapt the files
/usr/local/c-icap/etc/c-icap.confand/usr/local/c-icap/etc/virus_scan.confto your needs. See the c-icap website for further information.Start the c-icap daemon:
/etc/init.d/c-icap startFrom now on, the daemon will automatically start every server reboot.
When using nevisAdmin v3, you can use the "Create" button within the operation view of the c-icap instance. This creates both, the configuration file for the c-icap daemon as well as the cron job entry shown in the chapter Update the virus signature database.
Configure nevisProxy
nevisProxy uses the ICAPFilter to forward HTTP requests and/or responses to the c-icap server to be validated by ClamAV. Example for request validation (content type application/.*):
<filter>
<filter-name>ICAPUploadFilter</filter-name>
<filter-class>ch::nevis::isiweb4::filter::icap::ICAPFilter</filter-class>
<init-param>
<param-name>ErrorCode</param-name>
<param-value>403</param-value>
</init-param>
<init-param>
<param-name>BufferRequest</param-name>
<param-value>true</param-value>
</init-param>
<init-param>
<param-name>RequestBufferSize</param-name>
<param-value>100000000</param-value>
</init-param>
<init-param>
<param-name>AllowRequestModification</param-name>
<param-value>false</param-value>
</init-param>
<init-param>
<param-name>ScanRequestHeaderCondition</param-name>
<param-value>Content-Type:application/.{*}</param-value>
</init-param>
<init-param>
<param-name>SplittMultipartBody</param-name>
<param-value>true</param-value>
</init-param>
<init-param>
<param-name>ScanRequest</param-name>
<param-value>true</param-value>
</init-param>
<init-param>
<param-name>InetAddress</param-name>
<param-value>localhost:1344</param-value>
</init-param>
<init-param>
<param-name>TargetURI</param-name>
<param-value>
/srv_clamav?allow204=on&sizelimit=off&mode=simple
</param-value>
</init-param>
</filter>
See the nevisProxy reference guide for more information about the ICAPFilter options.
Update the virus signature database
The virus database files (.cvd/.cld) of ClamAV are stored in the /var/lib/clamav/ directory. You can use the freshclam utility to update these database files.
Configure the file
/etc/freshclam.conf. For example, by setting the right DatabaseMirror to use or the HTTPProxyServer required to connect to the internet. For additional documentation and limitations with the public mirrors, see the official ClamAV documentation./etc/freshclam.conf# ...skipped...
DNSDatabaseInfo current.cvd.clamav.net
# ...skipped...
DatabaseMirror db.XY.clamav.net
DatabaseMirror database.clamav.netReplace XY in DatabaseMirror with your country code, for example: CH.
Run freshclam once manually to initially load the definitions. Observe possible errors. It is expected that this call runs successfully without errors.
freshclamConfigure a nightly cronjob to update the virus database files regularly.
echo "0 5 * * * sudo /usr/bin/freshclam \
--quiet -l /var/log/clamav/freshclam.log 2>/dev/null" \
>> /var/spool/cron/nvluser