Number Matching
The number matching feature serves to prevent MFA (multi factor authentication) fatiuge attacks.
MFA push fatigue attack, also known as MFA Bombing or MFA Spamming, is a type of social engineering cyberattack. In this strategy, attackers repeatedly send second-factor authentication requests to the target victim registered devices. The attack relies on users approving simple push notifications without knowing the context of the session they are authenticating.
Overview
If number matching is used when triggering out-of-band authentication via push message in the server, the application asks the end-user to provide some digits. The operation will only continue if the user enters the correct digits displayed on the screen into the Access App.
It is important to present the end-user enough information in both the web application (where the out-of-band authentication is started) and the Access App about the necessary digits. In the Access App, the label number_matching_screen_description in the localizations file contains context information that helps to define the required digits.
If the user provides invalid digits, the authentication will fail.
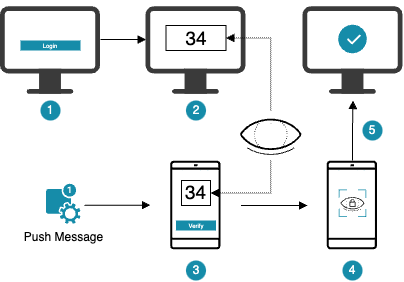
- The user performs a login or transaction confirmation, a push message is sent to the Access App.
- The browser shows a random, two digit code.
- The user enters the code displayed in the browser in the Access App and confirms the entry.
- If the code matches, the user can continue with the operation.
- The user completes the operation.
For additional conceptual information, refer to the following chapters in the concept guide:
- Channel Linking contains information regarding the number matching concept from the backends point of view. Number matching is a specific subset of channel linking.
For additional technical information, visit the following chapters in the reference guide:
- Out of Band FIDO UAF Auth State contains information of how to configure the nevisAuth auth state.