Deployment via SSH
In a classic deployment, nevisAdmin 4 deploys configuration to hosts that run Nevis components via SSH.
The following diagram shows a minimal setup of nevisAdmin 4, including two managed hosts.
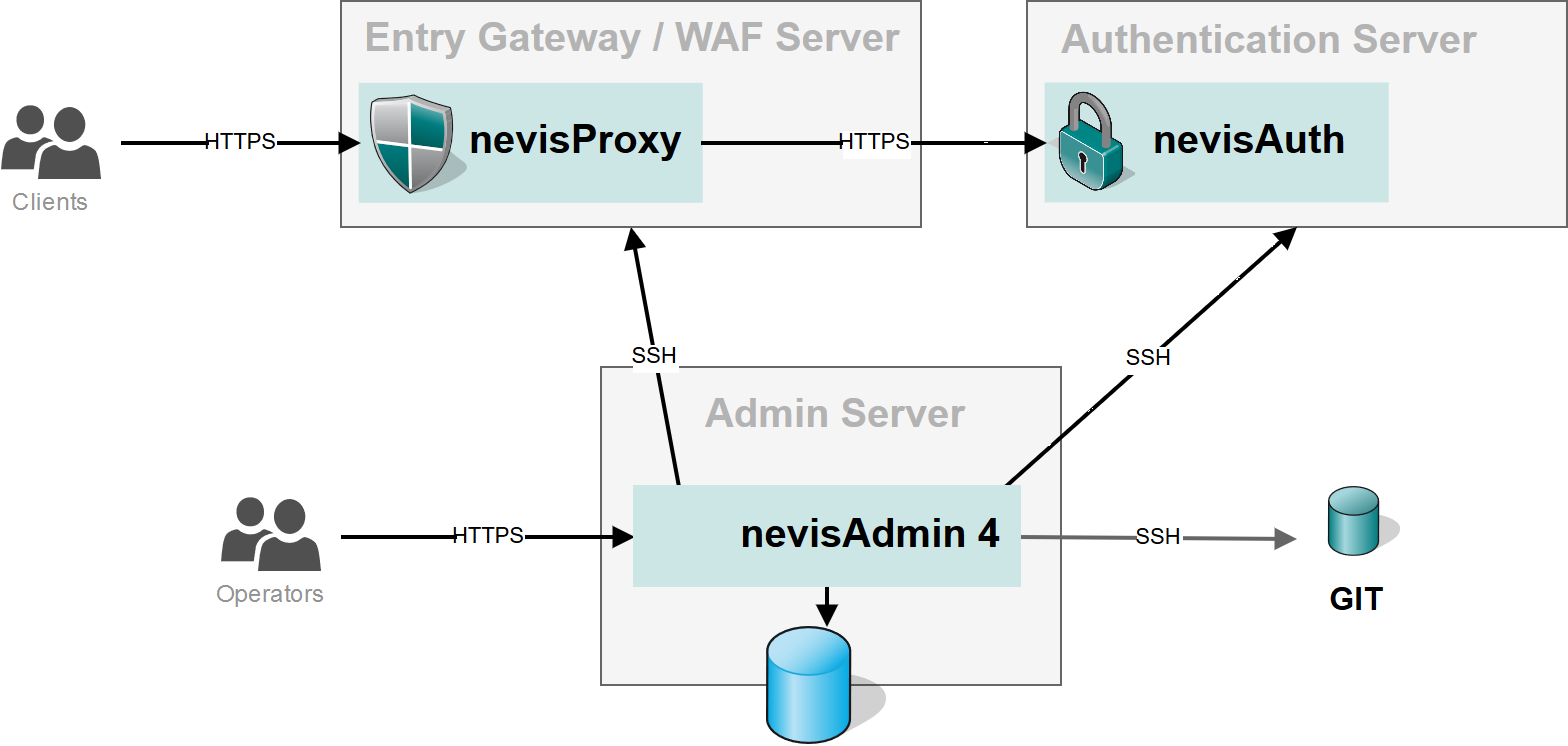
To establish an SSH connection to remote hosts, nevisAdmin 4 provides two methods:
- private key authentication (recommended), or
- authentication via username and password, which can be different for each host.
Both options are described in more detail below.
The complete process to set up SSH and deploy a configuration is as follows:
- Choose your authentication method and follow the instructions below.
- If needed, configure host connection variables in your inventory.
- To perform the deployment, see:
- Deployment of the configuration using the GUI.
- Generation Engine for command-line based deployment.
The connection user must have sudo permissions as well as permissions to change the owner, group and permissions of deployed files. You can take, for example, the users root or nvluser for deploying on nevisAppliance hosts.
SSH is the only deployment protocol supported by nevisAdmin 4. The nevisAgent that was used by nevisAdmin 3 is not supported.
Private Key Authentication
For security reasons, we recommend using a private key for the SSH connections, instead of logging in with a password.
The private key must be the same for all hosts that you connect to.
You can define the path to the private key in the nevisadmin4.yml file. If not set, nevisAdmin 4 will use the private key of the runtime user nvbuser, which is located at /home/nvbuser/.ssh/id_rsa. If the target user is root, then you do not need to define host connection variables in the inventory. To login as another user, specify the global __connection_user inventory variable.
If there is no private key yet, create one using the following command:
su nvbuser
ssh-keygen -m PEM
Here is a simple configuration for nevisadmin4.yml which applies when the private key has no password:
nevisadmin:
deployment:
ssh:
privatekey:
file: /home/nvbuser/.ssh/id_rsa
Password protected Private Key
If the private key is password-protected, also set the passphrase in the nevisadmin4.yml file. Here is an example configuration:
nevisadmin:
deployment:
ssh:
known-hosts: /home/nvbuser/.ssh/known_hosts # optional setting to connect to known hosts only (if omitted, all hosts are trusted)
privatekey:
file: /home/nvbuser/.ssh/id_rsa
passphrase: password # The passphrase needed to access the private key file (required only if key is password protected)
After changing these settings in nevisadmin4.yml you need to restart nevisAdmin 4.
It is possible to retrieve sensitive values, such as passwords, from external sources. To do this, specify the following values instead of the password:
${env:<VAR_NAME>}to use an environment variable${exec:<shell command>}to run a shell command and use its output as the value
For example, assuming the environment variable IDENTITY_FILE_LOCATION and a script called get-password.sh are available:
nevisadmin:
deployment:
ssh:
privatekey:
file: "${env:IDENTITY_FILE_LOCATION}"
passphrase: "${exec:/home/nvbuser/bin/get-password.sh --password-key identity-phrase}"
Creating the known_hosts File
As an example, if you use the private key of the nevisAdmin 4 runtime user nvbuser, you can populate the known_hosts file as follows:
su nvbuser
ssh-copy-id -i <path-to>/id_rsa -o HostKeyAlgorithms=ssh-rsa <connection-user>@<host>
The location of the known_hosts file should be set in nevisadmin4.yml as follows:
nevisadmin:
deployment:
ssh:
known-hosts: /home/nvbuser/.ssh/known_hosts # optional setting to connect to known hosts only (if omitted, all hosts are trusted)
Username / Password Authentication
An alternative option for the connection to remote hosts is to define a username and password for each host.
The remote username and the password are defined in the inventory. See Configuring Host Connections for details.