Authentication
Nevis Mobile Authentication supports two authentication use cases:
- In-band authentication For more information, see In-Band Authentication in the Nevis Mobile Authentication Concept and Integration Guide.
- Out-of-band authentication For more information, see Out-of-Band Authentication in the Nevis Mobile Authentication Concept and Integration Guide.
nevisAdmin 4 provides two patterns to configure these use cases:
In-Band Authentication
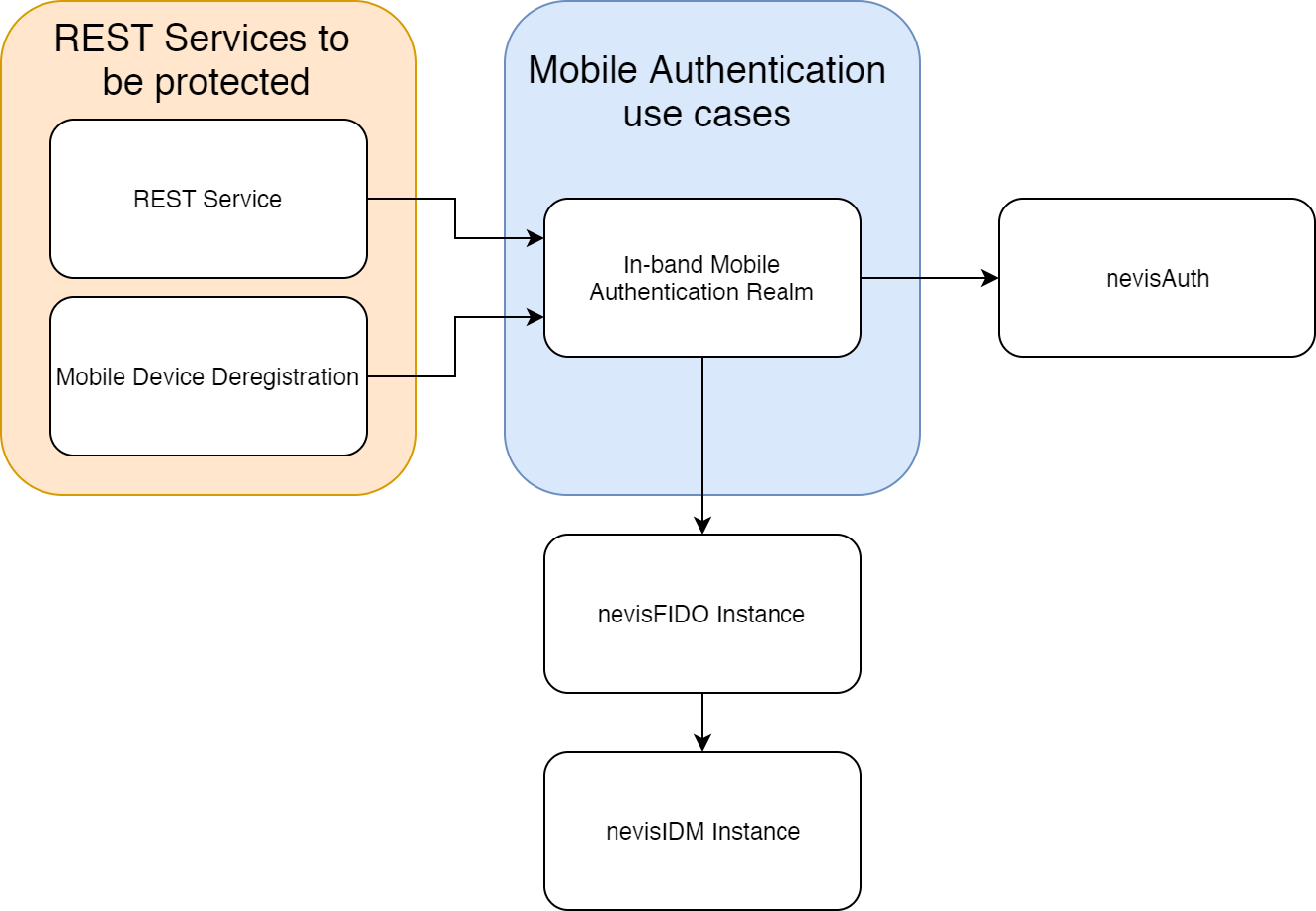
You use the In-band Mobile Authentication Realmpattern to protect a backend resource used by a mobile application (for example a REST Service). The pattern is similar to a regular Authentication Realm pattern, however limited to the protection of REST Service or Mobile Device Deregistration patterns.
The next figure shows the connections of the In-band Mobile Authentication Realm pattern with other patterns:
The next movie shows how to configure in-band authentication to protect a REST Service, with the In-band Mobile Authentication Realm pattern:
Out-of-Band Authentication
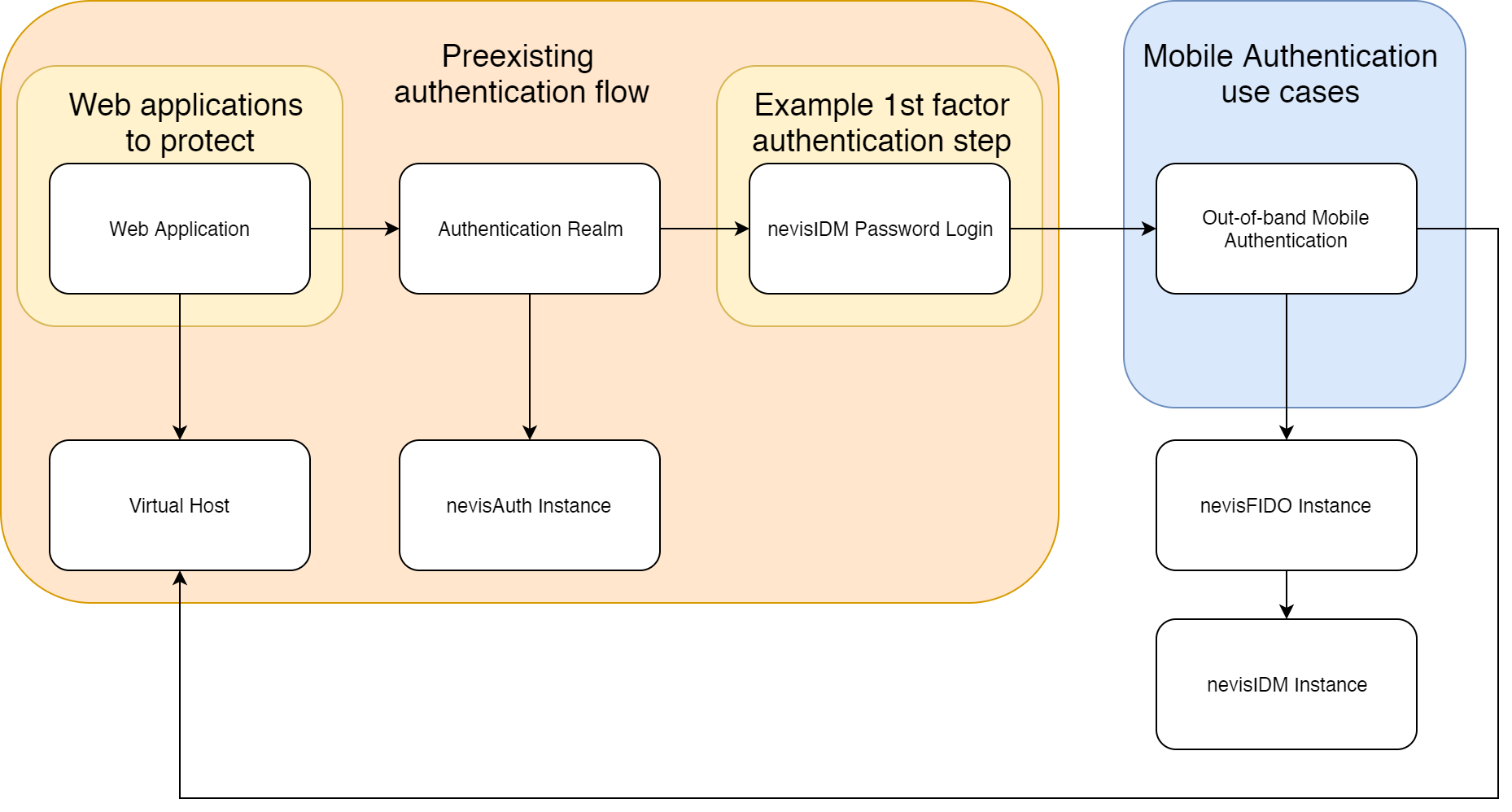
When a web application needs to be protected by mobile authentication, you can use the Out-of-band Mobile Authentication pattern.
The figure below shows a setup with out-of-band mobile authentication. The white text boxes represent the corresponding patterns.
The next sections explain how you can configure such an out-of-band authentication setup, including two-factor authentication.
Protecting Wikipedia with 1st factor nevisIDM Password Login
The first step is to configure a stable 1st factor authentication (see the following movie). This simulates a possibly already existent authentication flow. The next section shows how out-of-band mobile authentication fits in.
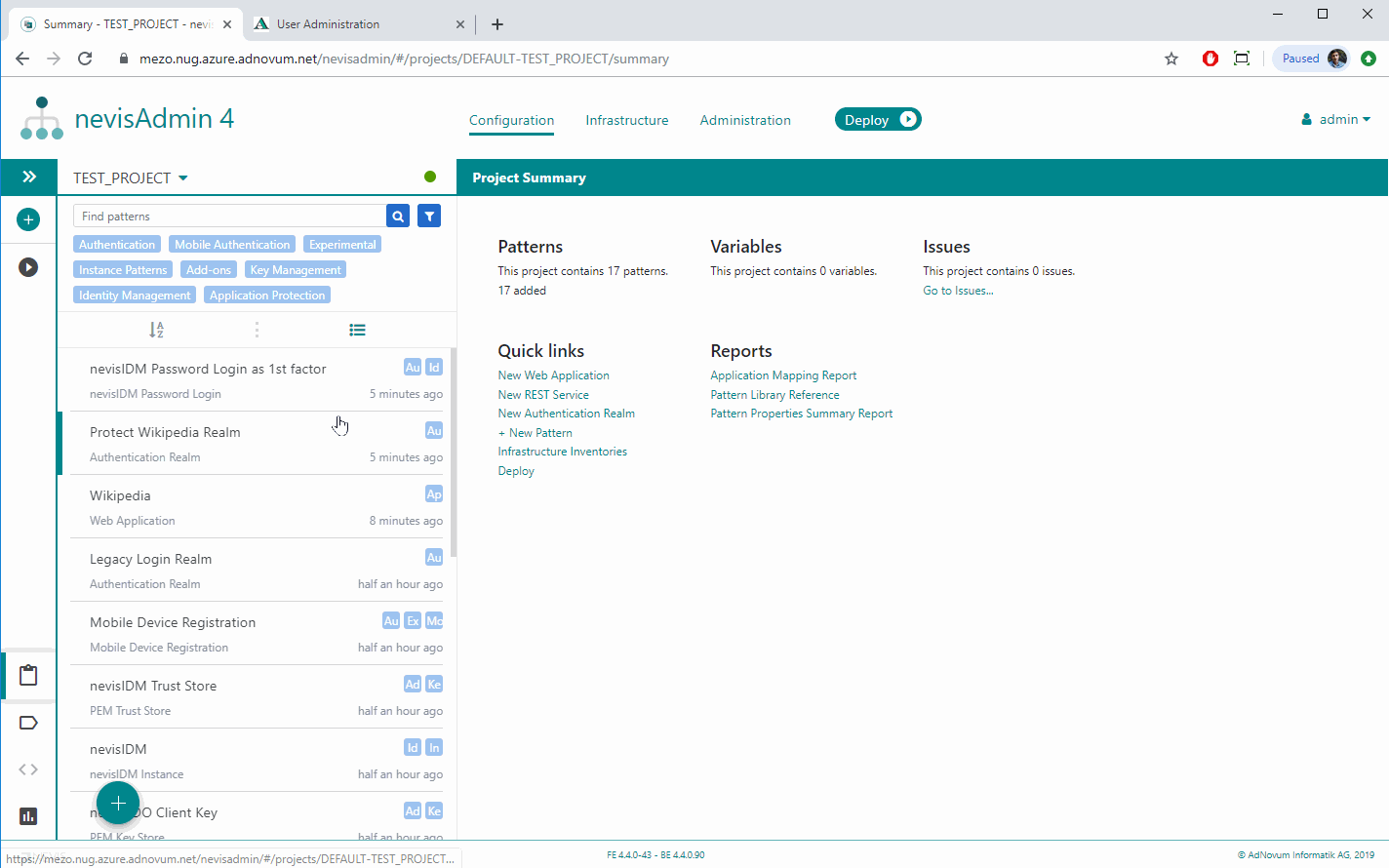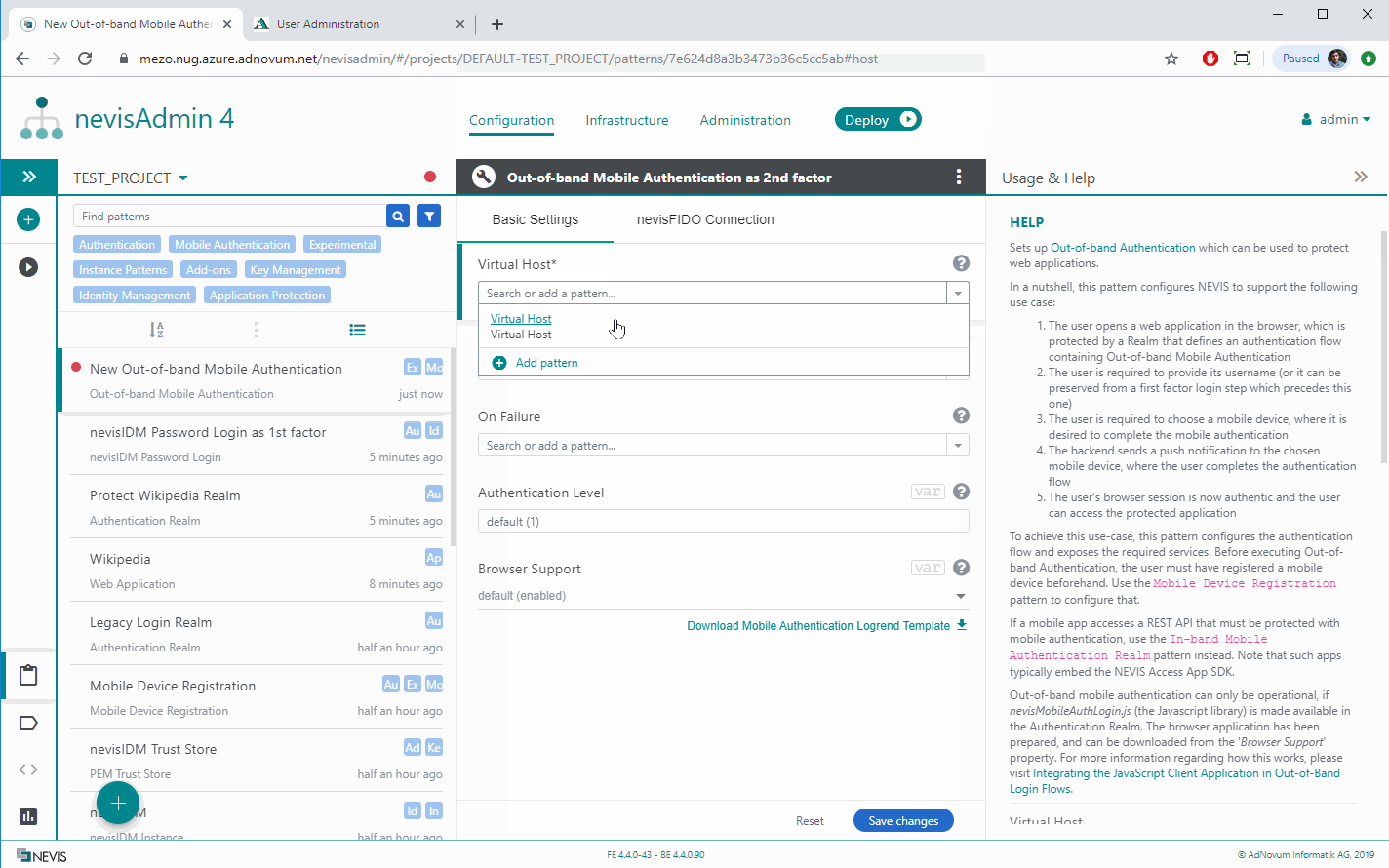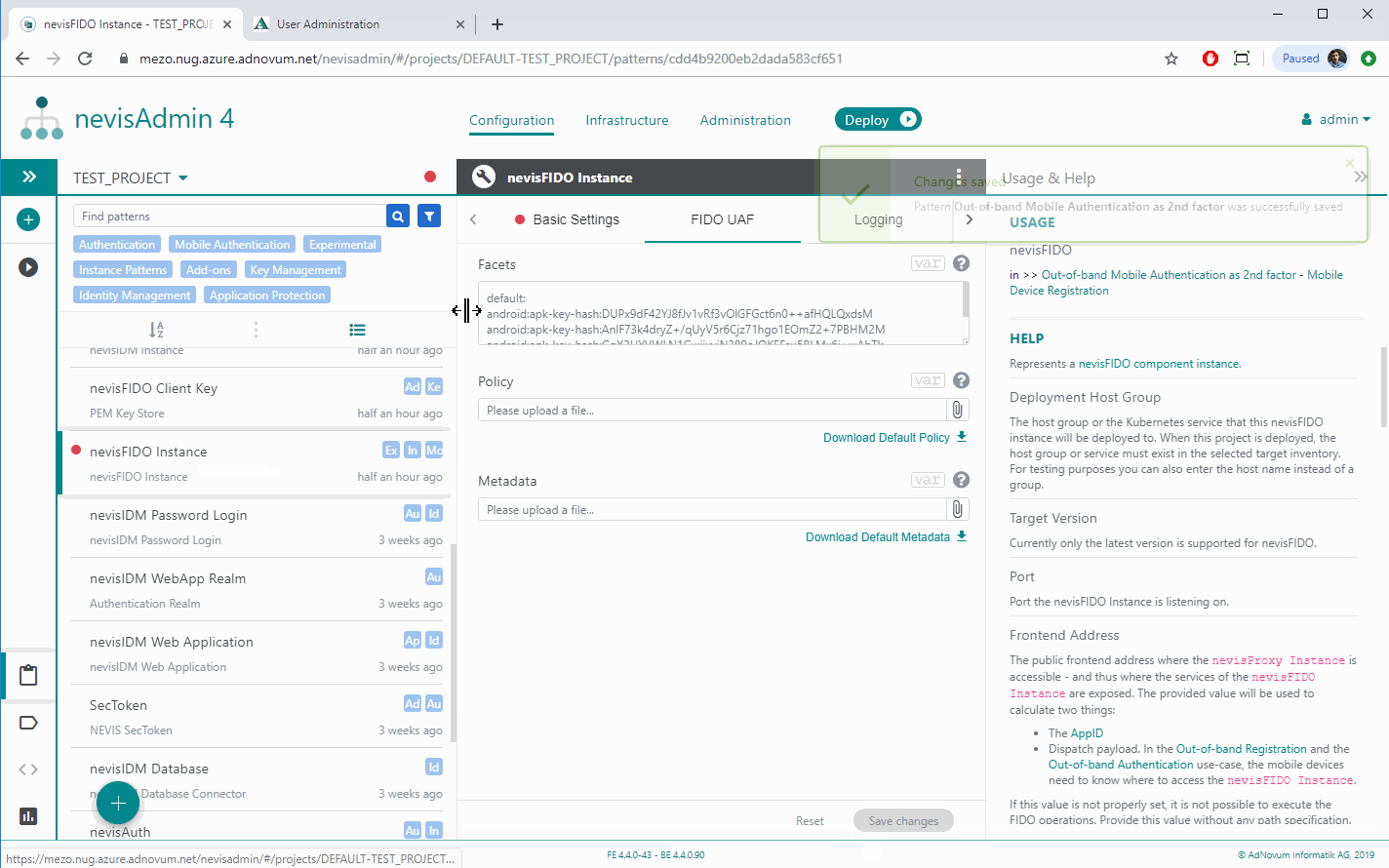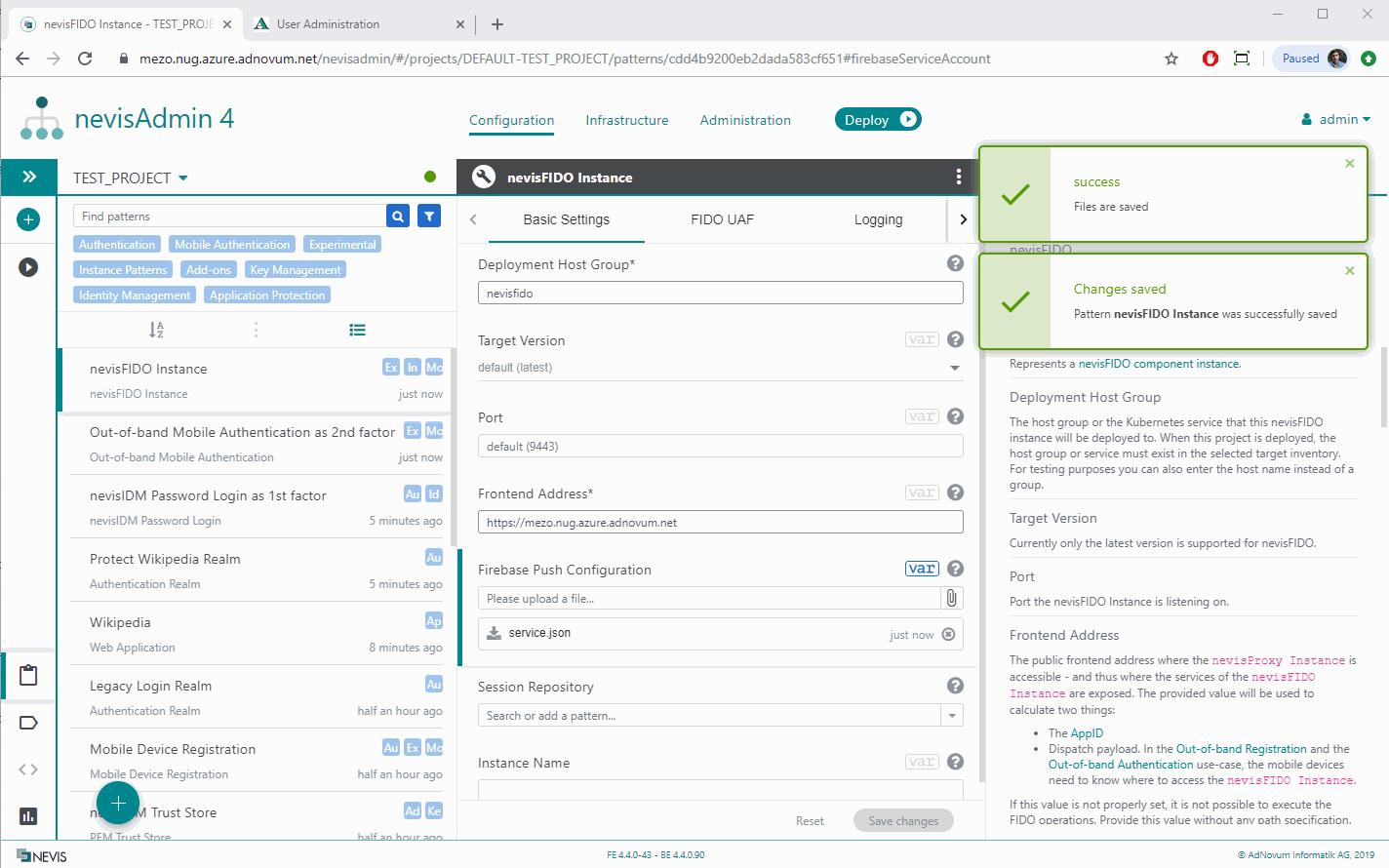
Adding Out-of-band Mobile Authentication as a 2nd factor
The second step is to configure out-of-band mobile authentication as the 2nd factor in our authentication flow.
As a precondition, you need to create a Firebase account and upload the generated service account onto the nevisAdmin 4 GUI. Firebase is a push message provider that sends out-of-band push messages to the mobile client application. For instructions on how to set up Firebase, visit `http://firebase.google.com/.
Out-of-band mobile authentication is designed to fit into existing authentication flows. This example, for instance, integrates out-of-band mobile authentication as 2nd factor in the nevisIDM Password Loginauthentication flow that we set up in the previous step. The goal of this two-factor authentication process is to protect Wikipedia.
Configuring out-of-band mobile authentication as first factor, that is, without first asking for the user's password, is not recommended. The use case works such that the user provides the username first and receives a push notification on his or her mobile device afterwards - where the authentication flow is completed. Not protecting this use case with a first factor authentication enables unauthenticated parties to send push notifications to the user's mobile device.
The movie below shows how to configure out-of-band authentication as 2nd factor.
Advanced topic: Using custom login templates
This use case requires the authentication flow to handle some logic in the browser (for example selecting a mobile device), so you need to have this browser-side JavaScript integrated into the Nevis login page. If you are interested in the details, see Integrating the JavaScript Client Application in Out-of-Band Login Flows in the Nevis Mobile Authentication Concept and Integration Guide.
In nevisAdmin 4, you configure the JavaScript loaded by the login page via the Login Template property field of the relevant Authentication Realm (pattern). If you leave the Login Template field empty, you get the default template, which will automatically include the browser-side JavaScript required for Mobile Authentication.