Certificate login
As an alternative to the user authentication with user name and password, a certificate login may be enabled. This allows administrators to authenticate against the nevisAdmin web front-end using a user certificate, e.g., stored on a smart card. The following steps are required to disable password authentication and to enable certificate login.
Administrator
Make sure that you have added your personal user account which will be mapped to your certificate and that your account has administrative privileges (member of the group "admin").
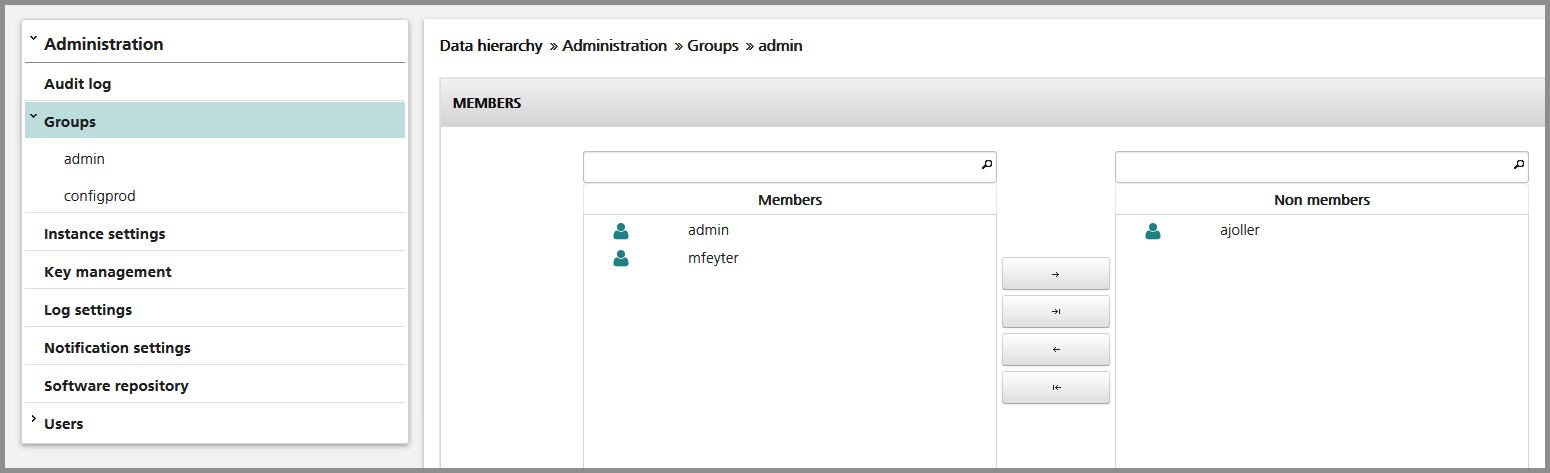
At least one administrator needs to be configured to finalize the certificate configuration.
JAAS configuration and certificate trust
Shutdown nevisAdmin before starting with the following configuration changes.
Afterwards, modify the following files:
/var/opt/nevisadmin/default/nevisadmin/config/cacerts.jk Add the CA certificates used to verify the client certificates to the Java truststore used by nevisAdmin. Example command to import a certificate:
Import CA certificateskeytool -import -keystore /var/opt/nevisadmin/default/nevisadmin/config/cacerts.jks \
-file /root/cacert.pem -alias clientauth/var/opt/nevisadmin/default/nevisadmin/applications/nevisadmin/WEB-INF/web.xml Change the authentication method from "FORM" to "CLIENT-CERT" within the web.xml file:
web.xml configuration snippet<login-config>
<auth-method>CLIENT-CERT</auth-method>
<realm-name>nevisadminRealm</realm-name>
<form-login-config>
<form-login-page>/views/login/login.xhtml</form-login-page>
<form-error-page>/views/login/error.html</form-error-page>
</form-login-config>
</login-config>/var/opt/nevisadmin/default/nevisadmin/config/login.conf Change the class name for the nevisadminRealm:
login.conf snippetnevisadminRealm {
ch.nevis.nevisadmin.container.jaas.NevisadminCertLoginModuleImpl required
realm=nevisadminRealm;
};/var/opt/nevisadmin/default/nevisadmin/config/domain.xml Modify the "certificate" realm within the domain.xml file by adding the "jaas-context" node:
domain.xml snippet...
</auth-realm>
<auth-realm
classname="com.sun.enterprise.security.auth.realm.certificate.CertificateRealm"
name="certificate">
<property
name="jaas-context"
value="nevisadminRealm"></property>
</auth-realm>
<auth-realm name="nevisadminRealm"
classname="ch.nevis.nevisadmin.container.jaas.NevisadminRealmImpl">
.../var/opt/nevisadmin/default/conf/nevisadmin.properties
The ch.nevis.nevisadmin.login.cert.subjectpattern property within the nevisadmin.properties file defines how the user name has to be extracted to the local users within nevisAdmin. This property's value is a regular expression applied against the subject field of the user's certificate.
The ch.nevis.nevisadmin.login.cert.createuser property allows you to enable the automatic creation of users when they log in for the first time.
Example patternch.nevis.nevisadmin.login.cert.subjectpattern=^CN=([a-z]+),O=SIVEN, C=ch$
ch.nevis.nevisadmin.login.cert.createuser=true
User authentication by certificate has now been enabled; you can start nevisAdmin again.
User to group mapping
Optionally, you may let nevisAdmin search the LDAP directory servers to fetch the user's group membership ("memberOf" attribute) and allow it to add users to the corresponding nevisAdmin groups automatically.
First, you have to configure your LDAP directory servers within the administration tab. You have to configure your LDAP server.
The following attributes need to be defined:
- LDAP server url: The schema, host and port of the LDAP server.
- Example: ldaps://ctxdc01.siven.ch:636/
- Base DN to search users: DN where the user objects are located within the LDAP directory server.
- Example: CN=Users,DC=ctx,DC=local
- Object filter to select the user LDAP filter which consists of an LDAP attribute name and the user's account id. The account id must be represented by the variable name ${userid} (this variable is replaced by the user id while searching the LDAP server).
- Example: sAMAccountName=${userid}
- Technical user DN to bind: Distinguished name of the user which is used to authenticate against the LDAP server.
- Passphrase of the technical user: Passphrase of the technical user which is used to authenticate against the LDAP server.
If you are using LDAPS, you also need to import the CA certificate to verify the LDAP server's certificate (if it is different from the CA certificate you have imported according to the figure Import CA certificates in the chapter JAAS configuration and certificate trust).
keytool -import -keystore/var/opt/nevisadmin/default/nevisadmin/config/cacerts.jks \
-file /root/cacert.pem -alias ldaps
Second, you have to define which "memberOf" attribute should be mapped to which group within nevisAdmin. This is done directly in the group view. Each group is mapped to one LDAP DN.
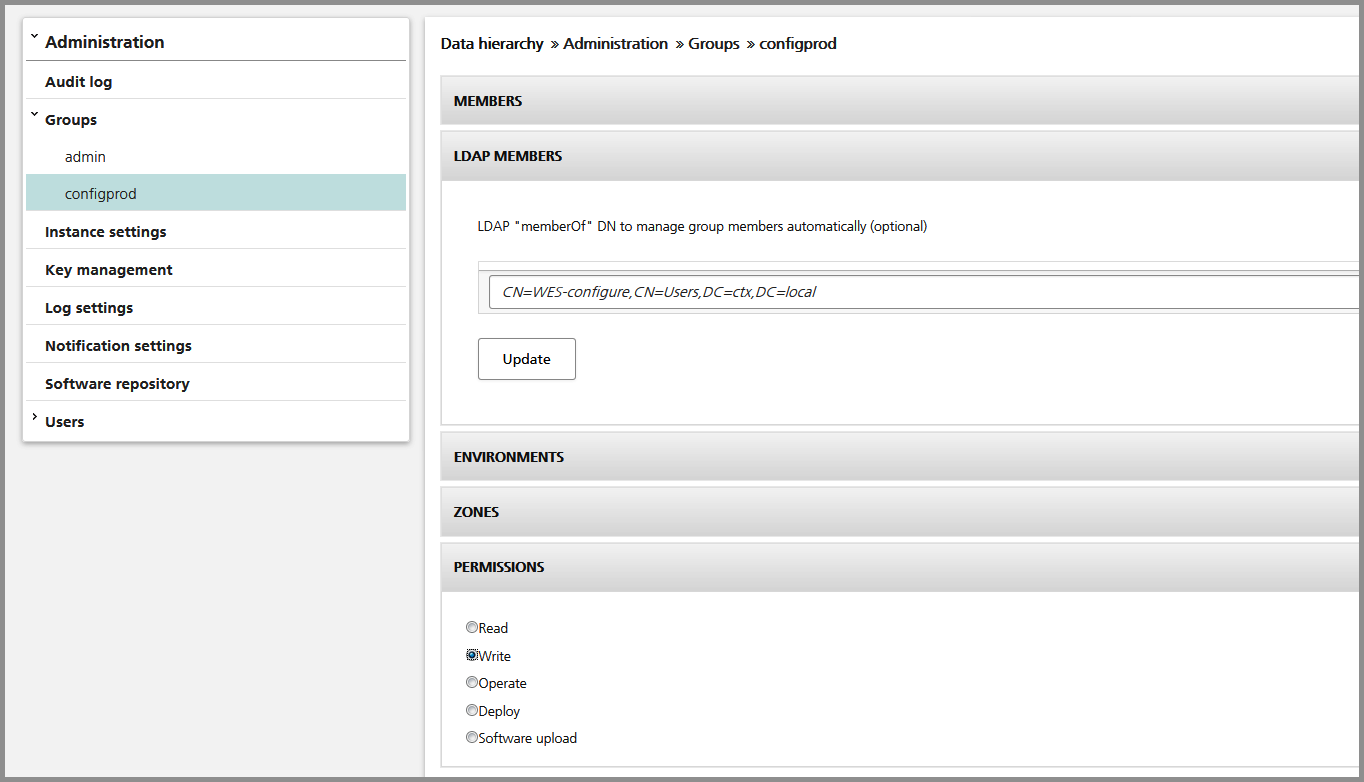
Members of groups having the "LDAP members" panel configured are automatically managed by nevisAdmin (whenever a user authenticates, he is added to or removed from the corresponding groups). Groups without an "LDAP members" DN are managed manually.