Certificate login using an LDAP directory
To authenticate users based on their certificates, two components are required:
- nevisProxy performs a two-way SSL handshake to ensure that the user is the owner of the certificate which shall be used for authentication and forwards it to nevisAuth.
- nevisAuth can search an LDAP directory server for the user's certificate. You may search for any attribute within the user's certificate, such as his common name (CN) or the certificate's serial number.
Firstly, you need to upload the CA root and intermediate CA certificates issuing client certificates to nevisProxy. Use the "CA certificates for client authentication" panel within the Key Management view of your environment as shown in the figure: Managing the certificates for the nevisProxy service, in the chapter: nevisProxy key material. These certificates will automatically be installed on the involved nevisProxy instances.
Secondly, you have to configure a realm. The first AuthState shall be a "X509Login" state used to extract the user's identity from the certificate and to perform additional certificate validation, such as checking it against the certificate revocation lists (CRL). A "TransformAttributes" can be used to extract any attribute from the certificate.
The following example shows how to extract an attribute from the certificate's subject:
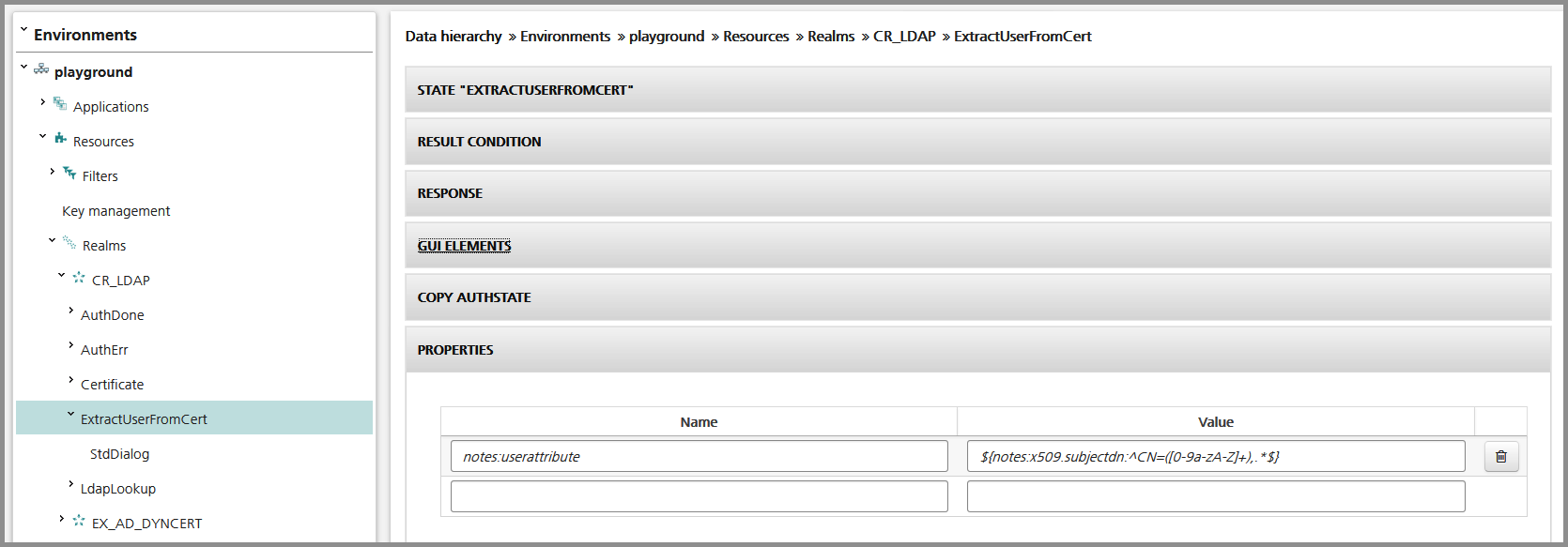
Next is an "AttributeDelegater" AuthState which is used to look up the user within the LDAP repository and to fetch additional attributes.
You may use the configuration template "Certificate login against an LDAP directory server" to configure this use case. For more information, see the chapter: Certificate login against an LDAP directory server.