LDAP authentication with Microsoft Active Directory
User authentication against a Microsoft Active Directory (AD) is performed in two steps:
- Bind with a technical user and locate the user's distinguished name (DN) with a tree search, searching for the "sAMAccountName" attribute from the configured userBaseDN.
- Bind against the AD using the resulting DN and the password entered by the user.
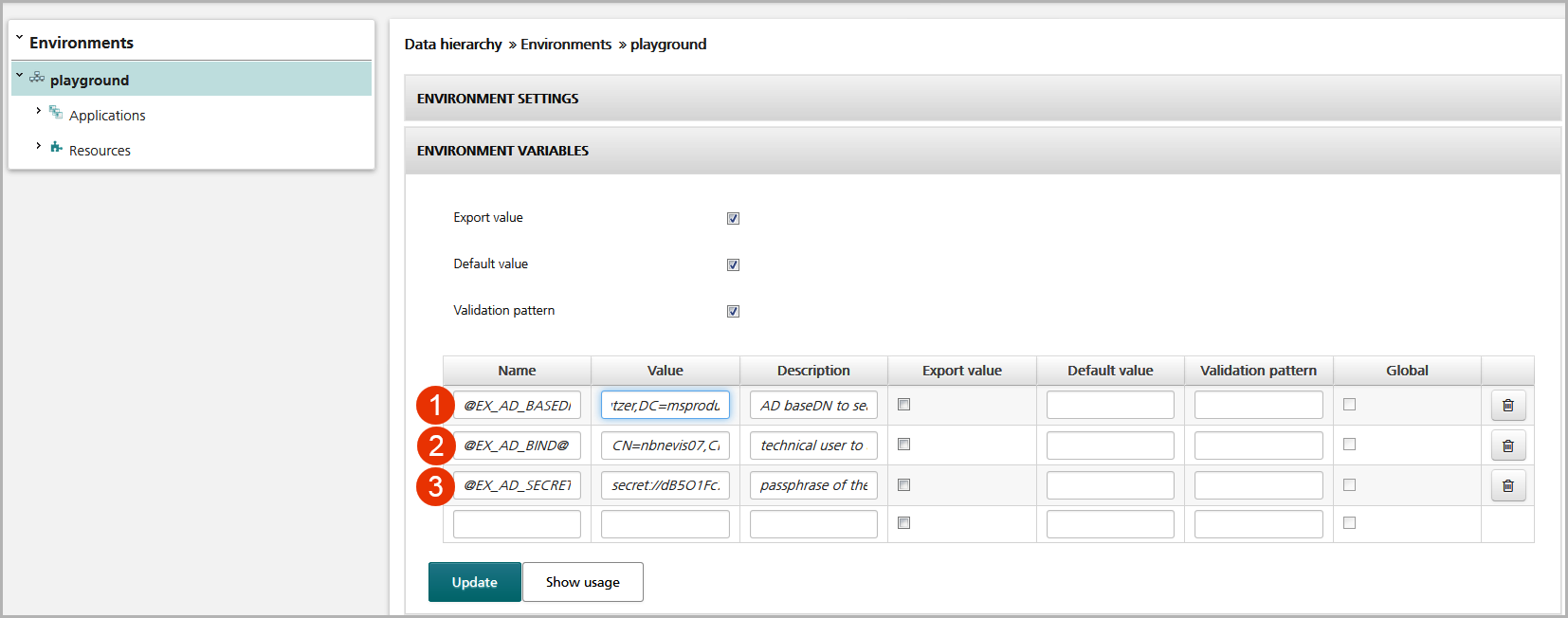
The figure below shows the parameters needed to perform a user authentication against an AD server. You find them in the Environment Variables panel in the view of the relevant environment (Configuration tab). No.1 in the figure shows the distinguished name of the technical user, no.2 displays the base DN to search for the user, and no.3 represents the passphrase of the user, which has been obfuscated with the nevisAuth encSecret command.
You may use the configuration template "MS Exchange using dynamic certificates" to configure this use case. For more information, see the chapter: MS Exchange using dynamic certificates.
Dynamic certificates
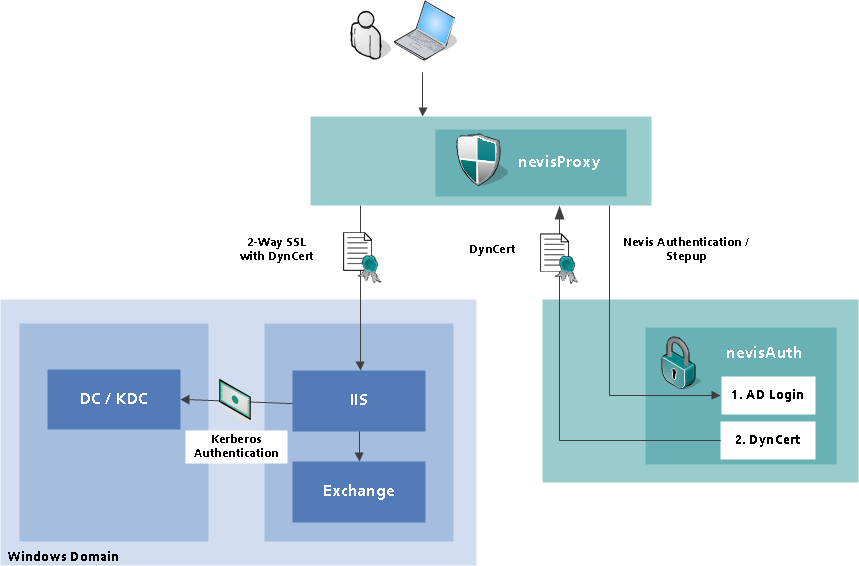
The dynamic certificate authentication system implemented in nevisProxy and nevisAuth requires the creation of a Certification Authority (CA). This CA is used by nevisAuth to create certificates for each authenticated user. The certificate used by nevisAuth must be installed in the Exchange server hosting the Internet Information Service (IIS).
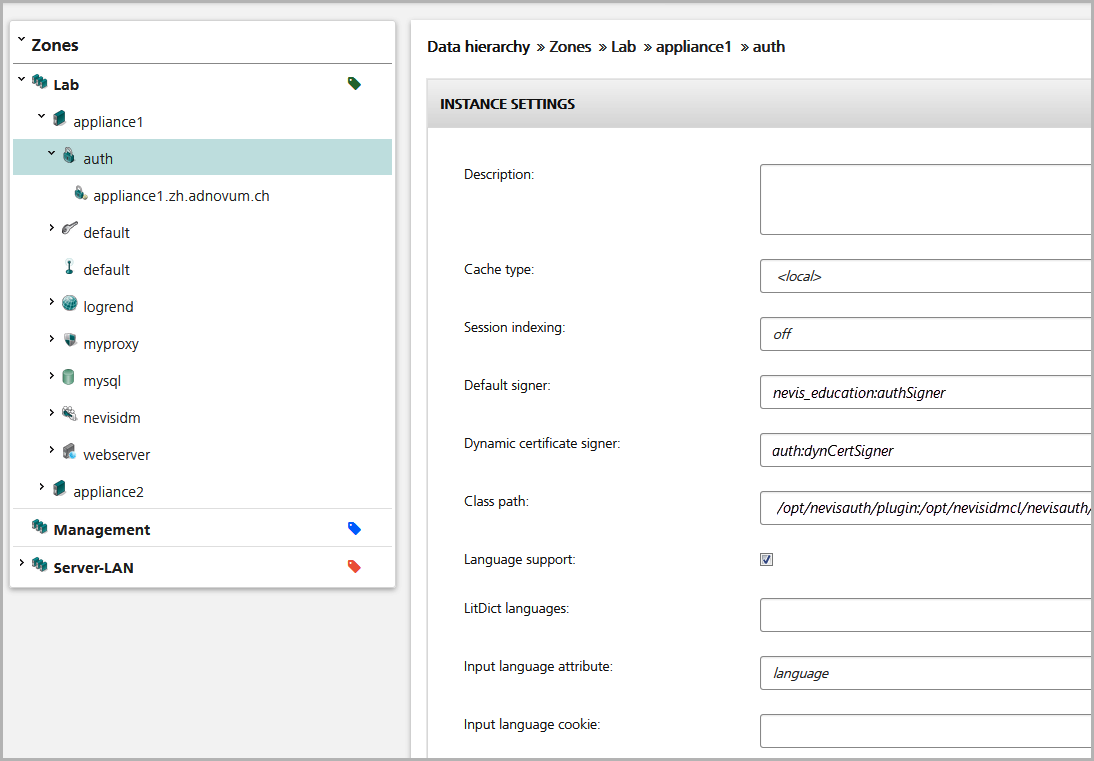
The table below shows how to create a new CA on the command line interface of the server hosting nevisAdmin. This example creates a new slot called "auth". The commands will prompt you to enter a passphrase to protect the key material.
# neviskeybox cacreate -ca "BoxDynCA
# neviskeybox import -slot auth -label dynCertSigner \
-file /var/opt/neviskeybox/default/NevisBoxDynCA/ca_key.pem
# neviskeybox import -slot auth -label dynCertSigner \
-file /var/opt/neviskeybox/default/NevisBoxDynCA/ca_cert.pem -own
# neviskeybox passwd -slot auth -label dynCertSigner -keep
# neviskeybox access -slot auth -label dynCertSigner -user nvauser -group nvbgroup
You can now import this nevisKeybox slot called "auth" to all servers hosting the involved nevisAuth instances as described in the chapter: Import key material, and set it to the nevisAuth instance to be used as the dynamic certificate signer.
The file /var/opt/neviskeybox/default/auth/dynCertSigner_certificate.pem contains the certificate to be installed on the IIS server.
The CA certificate must be configured on the domain controller to be trusted for the Active Directory and integrated for the authentication purposes in this domain. To do this, copy the CA certificate to the domain controller and issue the following command.
certutil -dspublish -f dynCertSigner_certificate.pem NTAuthCA
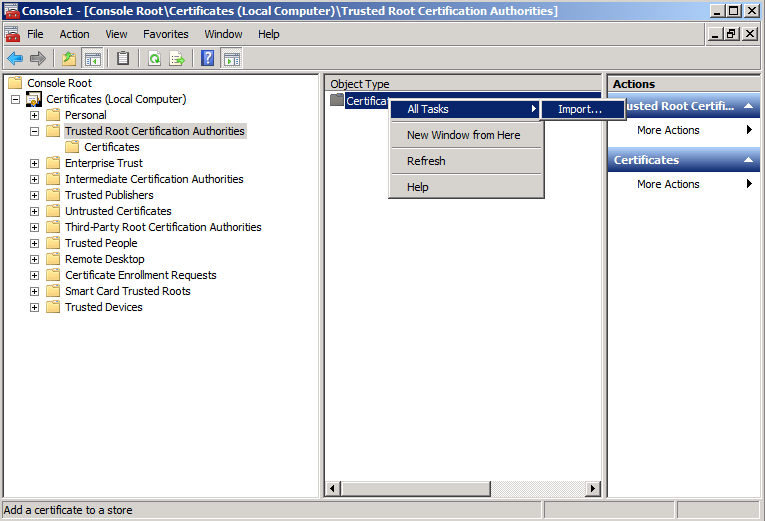
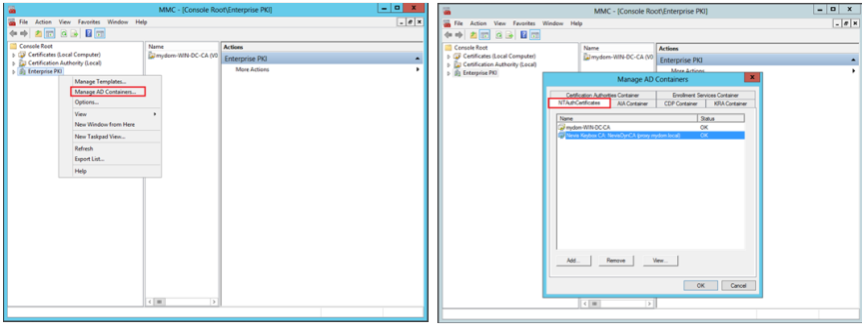
You may verify the settings within the Windows management console.
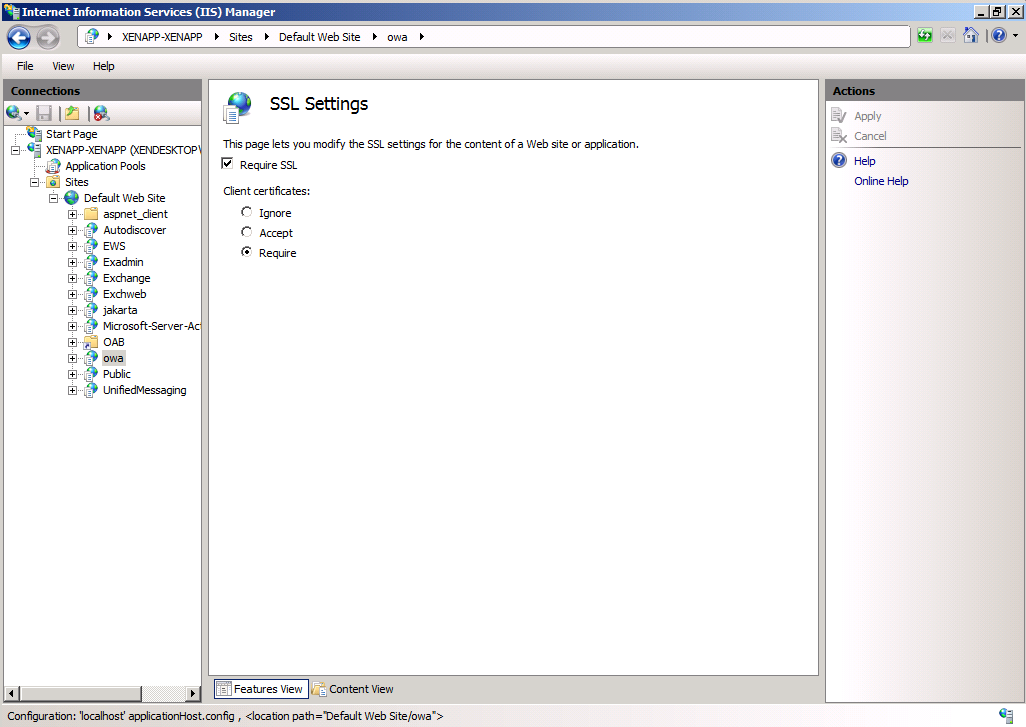
On the IIS server, the SSL settings must either be set to "require" or "accept", see the figure below. Ensure you enable the initial client certificate negotiation as described in the chapter: IIS - Initial Client Certificate Negotiation, in case you don't set the "require" option globally.
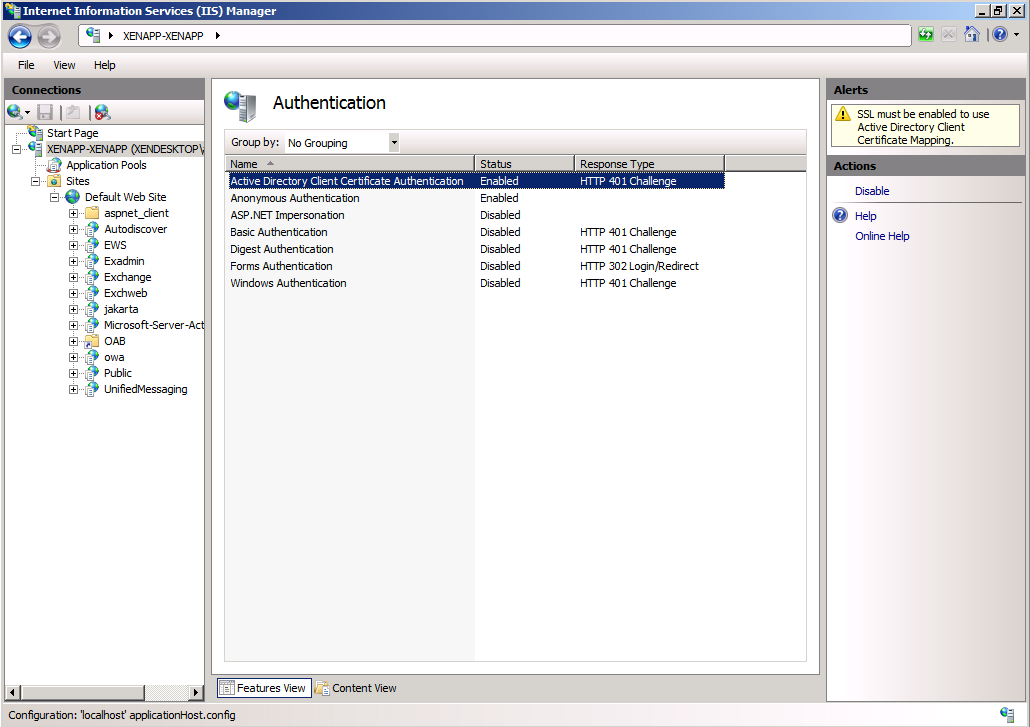
In addition, the "Client Certificate Mapping Authentication" must be enabled globally via the UI.
To ensure, that the "Client Certificate Mapping Authentication" feature is enabled for all applications, we recommend doing this by the following commands as shown in the code block below.
# cd c:\windows\system32\inetsrv
appcmd unlock config /section:clientCertificateMappingAuthentication
appcmd set config "Default Web Site/owa" -section:clientCertificateMappingAuthentication /enabled:true
appcmd set config "Default Web Site/Microsoft-Server-ActiveSync" -section:clientCertificateMappingAuthentication /enabled:true
appcmd set config "Default Web Site/ecp" -section:clientCertificateMappingAuthentication /enabled:true
appcmd set config "Default Web Site/ews" -section:clientCertificateMappingAuthentication /enabled:true
appcmd set config "Default Web Site/autodiscover" -section:clientCertificateMappingAuthentication /enabled:true
appcmd set config "Default Web Site/oab" -section:clientCertificateMappingAuthentication /enabled:true
appcmd set config "Default Web Site/rpc" -section:clientCertificateMappingAuthentication /enabled:true
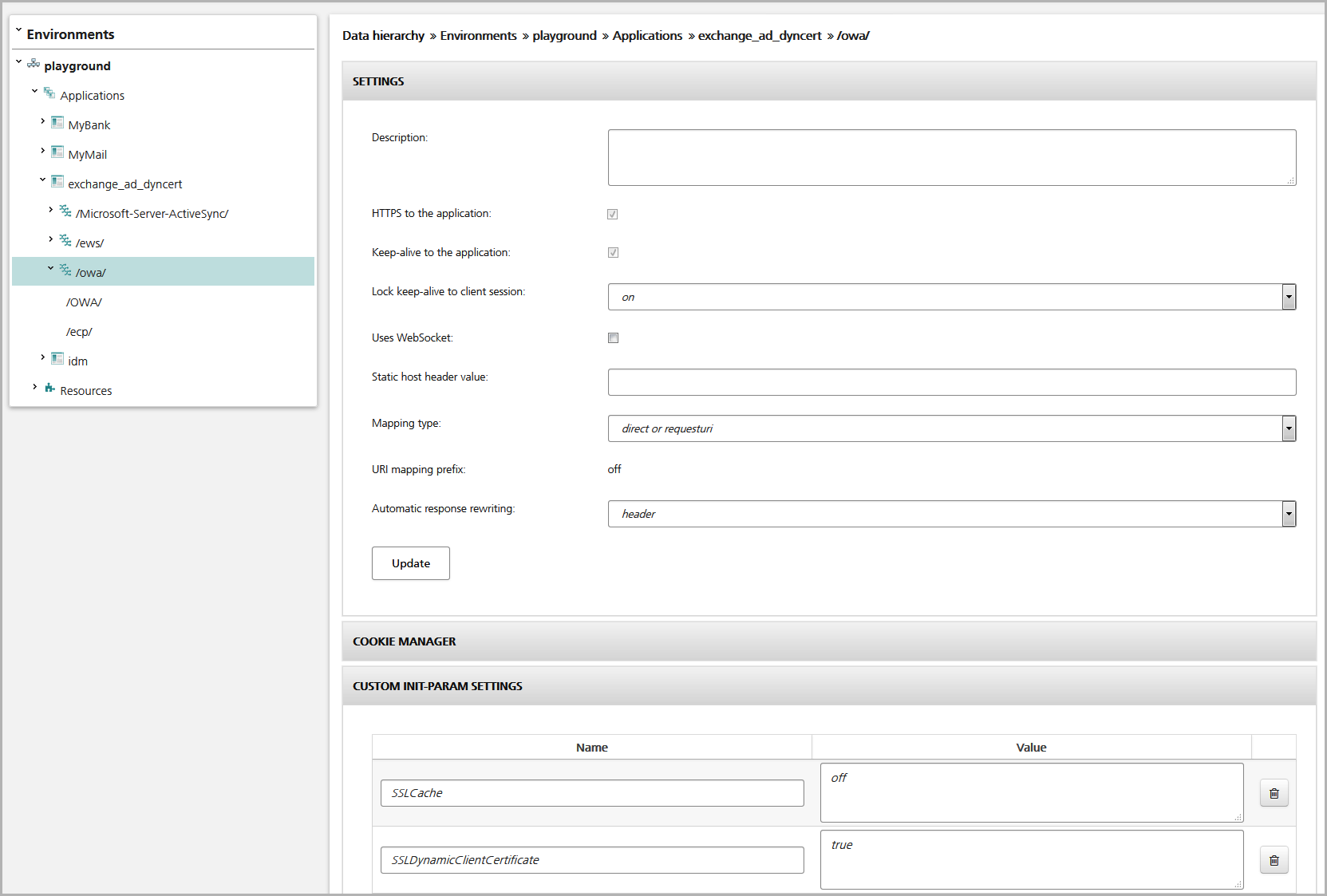
In the view of the application's mapping (Configuration tab), specify the following settings (see the figure: Enable dyncert and lock client session, below:
- Lock the TCP keep-alive of the back-end connections to the client session, by going to the Settings panel and selecting "on" in the Lock keep-alive to client session field.
- Enable the usage of dynamic certificates ("SSLDynamicClientCertificate"), by going to the Custom Init-Param Settings panel, and entering "SSLDynamicClientCertificate" in the Name field and "true" in the corresponding Value field.
Enable dyncert and lock client session:
IIS - Initial Client Certificate Negotiation
Enable initial client certificate negotiation for your Microsoft Internet Information Services (IIS). If the client certificate negotiation property is enabled, each time a new SSL connection is negotiated, the server will immediately negotiate a client certificate, preventing the server response 413 for large POST requests.
Initial client certificate negotiation may be enabled on two different ways:
For IIS 6 servers, respectively IIS servers with installed IIS compatibility libraries and tools, the SSLAlwaysNegoClientCert flag can be set by the following command:
Enable the SSLAlwaysNegoClientCert flagcscript adsutil.vbs set w3svc/1/SSLAlwaysNegoClientCert trueFor IIS 7 and above architectures, the
Negotiate Client Certificateparameter within the "sslcert" object must be set to "Enabled". This can be done using the "netsh http add sslcert" command. The "netsh http" command does not offer a "modify" option, but you may use the "show", "delete", and "add" commands to apply configuration changes.To enable the Negotiate Client Certificate parameter, first get the current settings. Afterwards you remove them and re-create the context again using the same parameters, but this time enabling the Negotiate Client Certificate parameter.
C:\> netsh htt show sslcert
## SSL Certificate bindings:
IP:port : 0.0.0.0:443
Certificate Hash : d658d1aa7e529e9ef66c902780d2acbad51a676d
Application ID : {4dc3e181-e14b-4a21-b022-59fc669b0914}
Certificate Store Name : My
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Enabled
Negotiate Client Certificate : Disabled
C:\> netsh http delete sslcert ipport=0.0.0.0:443
SSL Certificate successfully deleted
C:\> netsh http add sslcert ipport=0.0.0.0:443
certhash=d658d1aa7e529e9ef66c902780d2acbad51a676d
appid="{4dc3e181-e14b-4a21-b022-59fc669b0914}" certstorename=My
verifyclientcertrevocation=enable
verifyrevocationwithcachedclientcertonly=disable
usagecheck=enable
dsmapperusage=enable
clientcertnegotiation=enable
SSL Certificate successfully added
C:\> netsh htt show sslcert
## SSL Certificate bindings:
IP:port : 0.0.0.0:443
Certificate Hash : d658d1aa7e529e9ef66c902780d2acbad51a676d
Application ID : {4dc3e181-e14b-4a21-b022-59fc669b0914}
Certificate Store Name : My
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Enabled
Negotiate Client Certificate : Enabled