Multi-factor login
When multi-factor authentication is set up by the administrator, the user must first set up their login with username (email) and password as a primary authentication method.
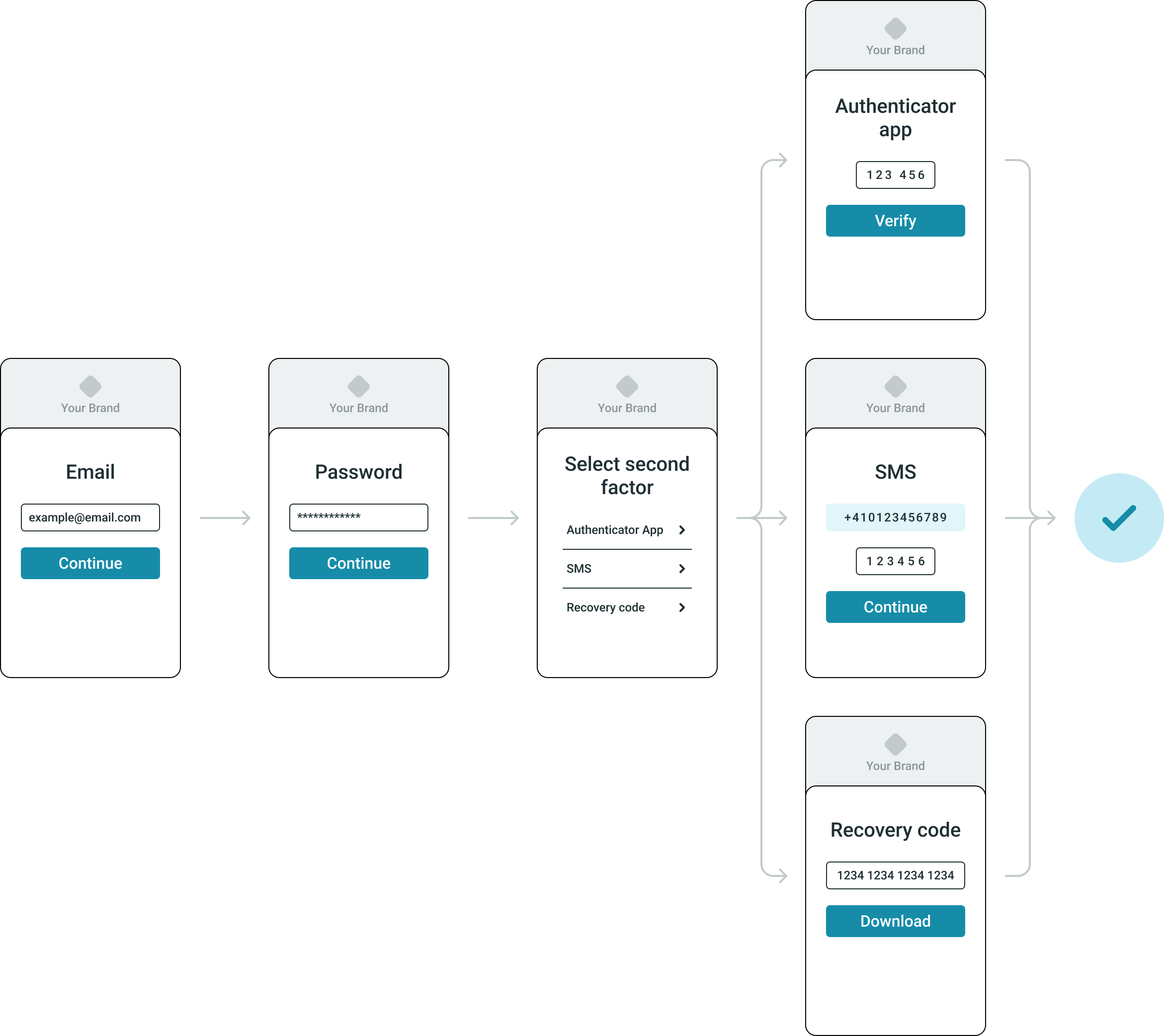
Once the primary authentication is set up, the user must set up at least one second-factor authentication method:
General information
After initial setup, the primary authentication step for the user is always to provide the username (email) and password. The secondary authentication options offered to the user depend on the following:
- The second-factor authentication method options enabled by the administrator in the Management console.
- The second-factor authentication methods the user sets up during signup.
When the administrator enables only one of the second-factor authentcation methods, the user can only set up and use that second-factor authentication method.
When the administrator enables both of the optional second-factor authentcation methods - time-based one-time password and SMS -, the user can set up and use either or both of these two second-factor authentication methods as secondary authentication.
As a fallback second-factor authentication method recovery codes are available by default and cannot be switched off in the Management console.
Primary authentication steps
The primary authentication for the user is always the authentication by username (email) and password:
- Go to the Identity Cloud login page.
- Provide the primary authentication by username (email) and password.
- Enter the username (email) registered to the account and click Continue.
- Enter the password for the account and click Continue.
The flow continues with the secondary authentication steps.
Secondary authentication steps
After the user completes the primary authentication steps, they have to complete the secondary authenticaiton steps.
If the user only set up one secondary authentication method, they are offered that one method by default - authenticator app or sms - and can opt to use recovery codes as a fallback.
If the user set up both secondary authentication methods - authentication app and SMS -, primarily they are offered to authenticate using the authenticator app. They can opt to authenticate with SMS, or to use recovery codes as a fallback.
To switch between authentication methods, the user can select the Try another way option on the secondary authentication page.
Authenticate by authenticator app
When the administrator enables time-based one-time password beside the default primary authentication method (username and password) and default fallback secondary authentication method (recovery codes), the login flow is as follows:
- If not offered by default, on the secondary authentication page click Authenticator app authentication method.
- Open the Authenticator app on the user device and locate the code generated by the authenticator app for this account.
- Enter the code on the Identity Cloud login page.
- Click Verify.
Authenticate by SMS
When the administrator enables SMS beside the default primary authentication method (username and password) and default fallback secondary authentication method (recovery codes), the login flow is as follows:
- If not offered by default, on the secondary authentication page select the Text message (SMS) authentication method.
- Open the text message sent to the mobile device containing the code.
- Enter the code sent in the text message on the Identity Cloud Text message page.
- Click Verify.
Authenticate by recovery code
- Select the Try another way option on the secondary authentication page.
- On the Select an authentication method page select Recovery code.
- Enter one of the recovery codes from the saved list of recovery codes.
- Click Verify.
Login with social identity provider accounts
- Go to the Identity Cloud login page and select the icon with the logo of the social identity provider of choice. The login page of the social identity provider loads.
- Go through the authentication flow of that social identity provider.
After successful verification, the user is logged into your application.
When providing the login details to a social account, the user completes the steps defined by the social identity provider. If you have any questions regarding the login flows of a social identity provider, turn directly to them for support.
Social identity providers
Social identity providers the administrator can add and enable are:
- Apple
- Microsoft